- Home
- Microsoft Intune and Configuration Manager
- Intune Customer Success
- Updates to the Windows Autopilot sign-in and deployment experience
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Update: Starting with Intune’s July (2207) service release, we’re excited to announce that some key Windows Autopilot functionality has been securely returned. Thanks to your patience and feedback, we were able to securely bring those features back. To learn more, see: Return of key functionality for Windows Autopilot sign-in and deployment experience for more information.
At Microsoft, we want to ensure that we are providing our customers with features that help to increase productivity and securely protect organizations. To improve the baseline security for Windows Autopilot, we recently made a few changes that affect new Windows Autopilot deployments:
- Users enter their credentials at initial sign-in during enrollment. While we no longer allow pre-population of the Azure Active Directory (Azure AD) User Principal Name (UPN) under the pre-provisioning landing page, any user targeting during pre-provisioning will still occur during the technician phase.
- For deployments where the profile is set to self-deploying mode (Public Preview) or pre-provisioning mode (formerly known as white glove, also in Public Preview), you cannot automatically re-enroll a device through Autopilot after an initial deployment in either of these modes. Instead, delete the device record in Microsoft Intune All Devices blade before re-deploying a device.
The intent of this post is to provide more context on why we made the changes and to provide links to documentation to help you be successful with your Autopilot experience.
Why did the Windows Autopilot team make these changes?
This was the biggest question we’ve received so far from customers. You liked, for example, giving a teacher a set of computers and using the welcome screen so the teacher could know which student to assign each device to. It’s a cool user experience when you assign a device, ship the device, and then the user opens that PC, and it welcomes them.
We loved the experience too! However, we made the changes because the reuse of hardware components, such as motherboards, or the refurbishment of devices without deregistration could potentially cause an issue if the device identifier can still be linked to a previous company. Hardware is being reused at record levels, partly due to the pandemic’s effect on global supply chains. While this reuse helps meet corporate sustainability goals, we had to remove the could and ensure no issues were caused. To date, we have found no evidence that anyone has used this to their advantage.
What’s next?
We are in the early design stages of an experience that customizes Autopilot enrollment. Using best practices from other enrollment workflows, we're looking at alternative solutions to reinstate this feature securely. Our goal is to improve your productivity and delight your users with what we bring back to the enrollment experience.
Additional Information:
- Getting Started with Autopilot deployments.
- Troubleshooting Autopilot deployments, including guidance how to resolve error code 0x80180014.
- MC288489 and MC289488 both address these changes. See this post for more information on staying up to date on Intune new features, service changes, and service health notices.
- The change to device re-enrollment only impacts users with reset or reused devices, and only for devices using self-deploying mode or pre-provisioned deployment. This change will not impact users with devices in user-driven mode. There is also no impact to current users whose devices were provisioned for the first time in self-deploying mode or pre-provisioning mode (no existing device record in these modes). We don’t anticipate additional changes to user-driven mode. This experience is different between user-driven mode and self-deploying mode or pre-provisioned deployment because of the enrollment mode used.
- To redeploy a previously provisioned device through Windows Autopilot (in self-deploying mode or pre-provisioning mode), first delete the device record from the All Devices blade in Microsoft Endpoint Manager. Be sure to not delete it from the Autopilot devices blade as that deregisters the device.
- For more on motherboard replacements, see Windows Autopilot motherboard replacement | Microsoft Docs.
- For CSPs/Resellers: You’ll need to request a communication process with your customer(s) to request that the device record be deleted when a deletion is required. We’re working to address and improve the customer experience for CSPs/Resellers and appreciate your feedback. Though we don’t have any ETAs currently, we’ll keep this post updated as soon as we have more information.
- Note that when initiating a “Wipe” remote action, the “Retain enrollment state and user account” checkbox should be unchecked to remove the device from Intune device management.
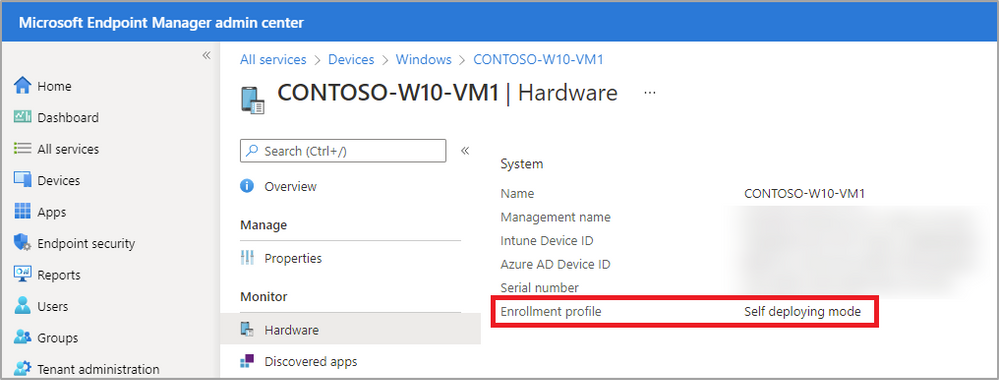
- To help troubleshoot/identify which Intune managed devices were enrolled via self-deploying or pre-provisioned mode, you can navigate to the Microsoft Endpoint Manager admin center > Devices > All devices > locate the impacted device > Monitor > Hardware > Enrollment profile.
If you have questions or comments for the Intune team, reply to this post or reach out to @IntuneSuppTeam on Twitter.
Post updates:
01/11/22: Updated Additional Information section.
02/24/22: Updated post with additional clarification that while the username or UPN will not be displayed, any user targeting during pre-provisioning will still occur during the technician phase.
- « Previous
-
- 1
- 2
- Next »
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.