
Extortion denial-of-service activity, the so-called RDDoS (ransom distributed denial-of-service) attacks have taken a tumble in the first quarter of the year, according to recent statistics from Cloudflare.
During a RDDoS attack, the threat actor hits a target company with large amounts of data to cause a service outage. The attacker then demands a ransom to stop the assault.
Ransom DDoS
Threat actors figured out that causing an outage could be a strong incentive for many companies to pay up to become operational again, especially organizations that risk a significant financial impact.
It should be noted that RDDoS attacks are launched by a different type of threat actors than ransomware gangs, who use DDoS to add more pressure on the victim on top of file encryption and the threat to publish stolen data.
Cloudflare reports that ransom DDoS attacks have dropped drastically in 2022, with only 17% of its DDoS-targeted clients reporting an extortion in January, 6% in February, and just 3% in March.
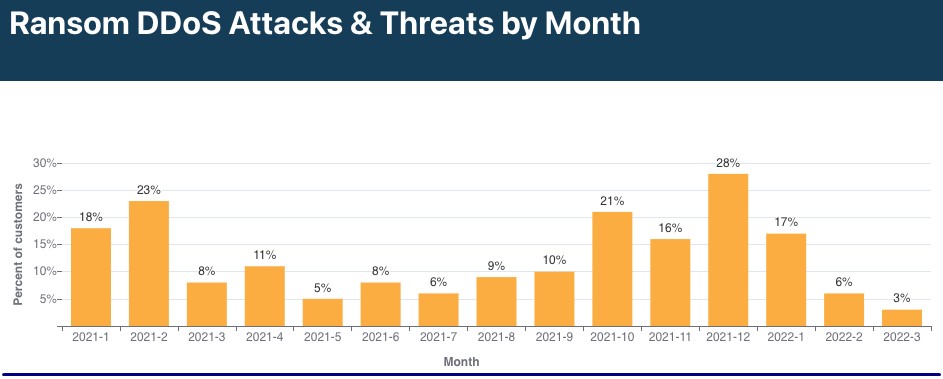
That’s a 28% decrease year over year and a 52% decrease compared to the last quarter of 2021 when ransom DDoS attacks spiked at 28% in the last month.
The reason for this drop remains unclear at this time.
First 2022 trends
On the rising trends reflected in Q1 2022 data, Cloudflare reports a whopping 164% YoY rise in application-layer DDoS attacks.
The most noteworthy trends within that category are a 5,086% QoQ increase in application-layer DDoS attacks against the consumer electronics industry and a 2,131% QoQ increase against online media firms.
Another concerning emerging trend is the reflection-amplification method, which we recently reported as something that has transcended theory and is already under active exploitation.
Reflection attacks start with a small packet reflected inside a closed network while its size gets amplified with each bounce. When reaching the possible upper limit, the resulting massive volume of traffic is channeled to the target.
An interesting in-the-wild exploitation case presented in Cloudflare’s report is that of the Lantronix Discovery Protocol being used in a large number of IoT devices.
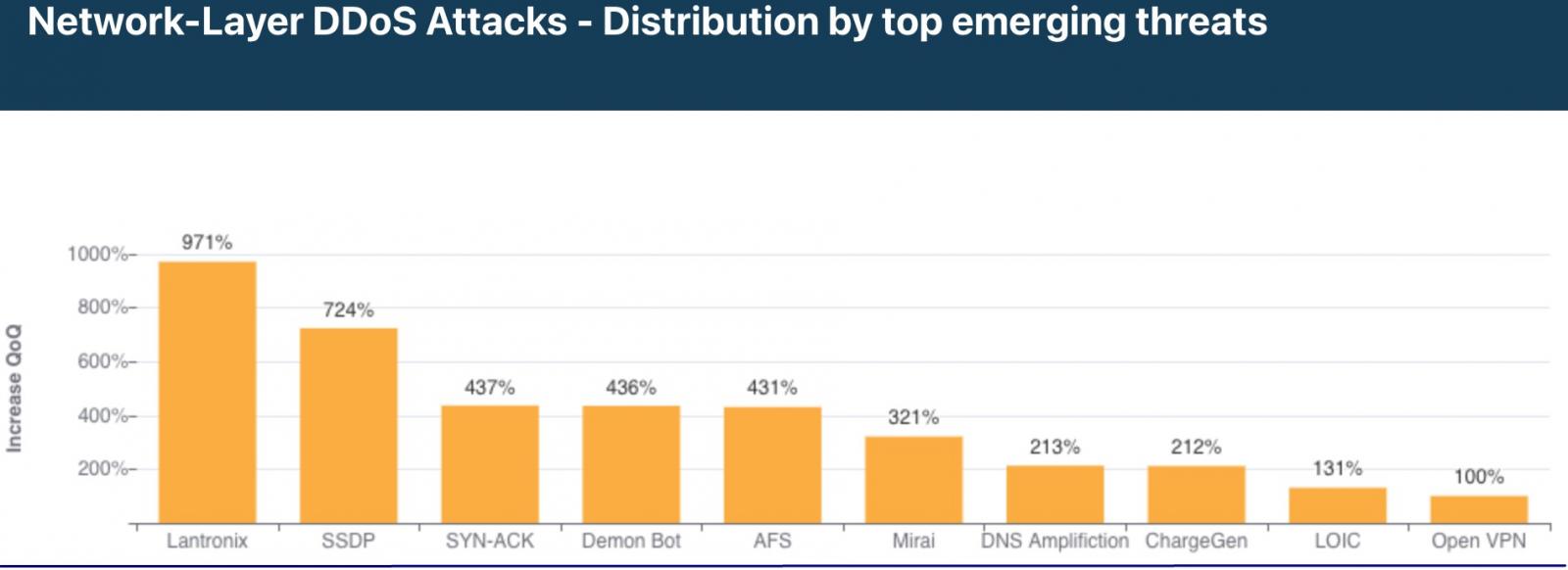
Attackers use 4-byte requests to target publicly exposed Lantronix devices, generating a 30-byte response, reaching an amplification ratio of 7.5x. While this is far from the most impressive ratio we’ve seen lately, it can still be very potent if large enough swarms of devices are recruited in these attacks.
By spoofing the source IP of the victim, the hackers can direct a large number of generated responses to a target, suddenly overwhelming them with an indirect attack.
Finally, Cloudflare reports a massive uptick in volumetric DDoS attacks, with those over 100 Gbps rising by 645% QoQ and those over 10 Mpps growing by over 300% QoQ.
As it has been the case for many years now, DDoS attacks aren’t going out of fashion but instead change form, methods, and traffic mixing tricks, and return to knock at the door of vulnerable, poorly protected, and weak servers.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now