- Home
- Security, Compliance, and Identity
- Microsoft Defender for Cloud Blog
- Microsoft Defender for Cloud PoC Series – Microsoft Defender for App Service
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Introduction
The purpose of this article is to provide specific guidelines on how to perform a proof of concept (PoC) for Microsoft Defender for App Service. This article is part a series of articles, called The Microsoft Defender for Cloud PoC Series, each providing specific guidelines on how to perform a proof of concept (PoC) for a specific Microsoft Defender for Cloud plan. For a more holistic approach where you need to validate Microsoft Defender for Cloud's CSPM and CWP capabilities, please read the How to Effectively Perform an Microsoft Defender for Cloud PoC article.
Planning
This section highlights important considerations and availability information that you should be aware when planning for the PoC. Let’s start with outlining how to go about planning for an Microsoft Defender for App Service PoC.
Important Note: At the time of writing this article, Microsoft Defender for App Service plan is available solely in Commercial clouds (and it’s not available in Sovereign cloud, such as US Gov and Azure China).
The first step begins with a clear understanding of the benefits that enabling Microsoft Defender for App Service brings to your organization. Microsoft Defender for App Service provides dedicated security analytics that help you identify a variety of threats to your App Service resources, based on monitoring of various relevant parts. Additionally, enabling Microsoft Defender for App Service assesses your App Service resources and provides security recommendations with detailed best practice guidance on how to harden those resources. To learn more about Microsoft Defender for App Service, watch this video.
Now that we’ve touched briefly on the benefits that Microsoft Defender for App Service brings, let’s move on to the next step. The second step is identifying which use cases the PoC should cover. A common use case might be detecting attempts to run high privilege commands on a Windows App Service, or maybe detecting when known malicious IP addresses connect to your Azure App Service FTP interface. Microsoft Defender for App Service monitors for many threats and its alerts cover almost the complete MITRE ATT&CK tactics from pre-attack to command and control. It can even detect DNS dangling – any DNS entries remaining in your DNS registrar when an App Service website is decommissioned. To learn more about threats can Microsoft Defender for App Service detect, read this article.
Keep in mind that you have 30 days free trial of Microsoft Defender for App Service, which means that you should plan to execute your PoC prior to this expiration and based on the results keep it enabled or not. Please note that once enabling the Microsoft Defender for App Services plan (as well as any other Defender for Cloud plan), it will stay enabled until you disable it.
Preparation and Implementation
This section highlights the requirements that you should be aware before starting the PoC.
There are two main steps when preparing to enable Microsoft Defender for App Service.
- Determining if the App Service plan is supported
At the time of writing this article, all App Service plans are supported, except Azure Functions on the consumption plan.
Important Note: Please visit this article, for the latest information about availability and list of supported App Service plans.
- Enabling Microsoft Defender for App Service on your subscription
Defender for Cloud natively integrates with App Service, meaning the integration is done in the backend and you don’t need to deploy (and/or onboard) any agents or additional software package (see Figure 1). To learn how to enable Defender for Cloud, read this article.
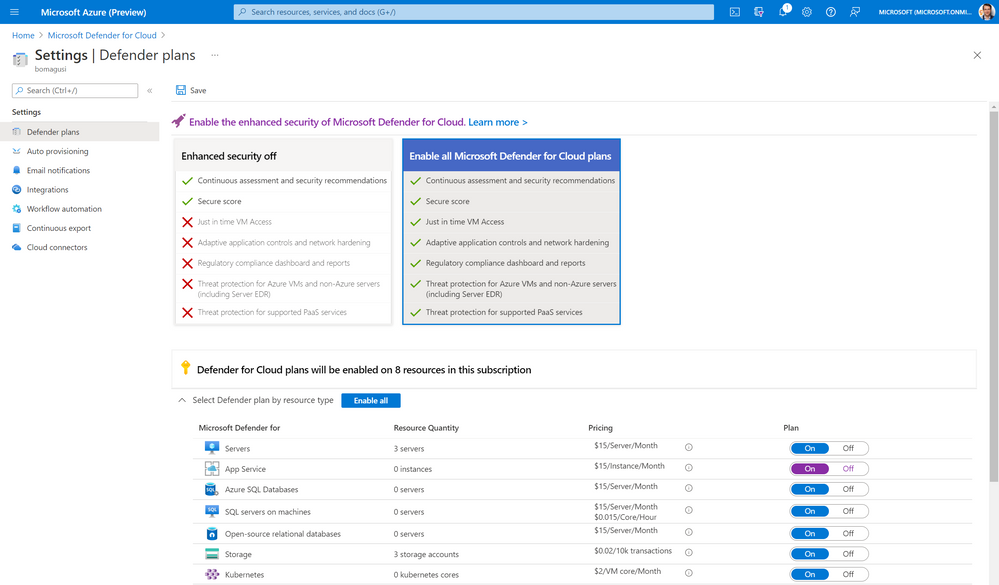
For the purpose of this PoC, it is important that you enable Microsoft Defender for App Service on the subscription(s) that you’ve identified for the PoC. Note: For the purposes of this PoC, it’s not mandatory to enable any other Defender for Cloud plans.
Validation
Once you’ve enabled Microsoft Defender for App Service on target subscription(s), you can validate it by simulating alerts relevant to the use cases that your PoC covers. You can also use the feature to validate Defender for App Service alerts (as show in Figure 2.).
When validating the alerts, be sure to consult the full list of App Service alerts.
- You can also export Defender for Cloud security alerts to a SIEM (i.e. Azure Sentinel or 3rd party SIEM).
- Learn more about how to stream alerts to a SIEM, SOAR or ITSM.
- Learn more about how to investigate Microsoft Defender for Cloud alerts using Azure Sentinel.
Check out the article on Validating Defender for Cloud Alerts for App Service.

Final Considerations
This article is all about providing specific guidelines on how to perform a proof of concept (PoC) for Microsoft Defender for App Service. For a more holistic approach where you need to validate Microsoft Defender for Cloud's CSPM and CWP capabilities, please read the How to Effectively Perform an Microsoft Defender for Cloud PoC article. As mentioned, Microsoft Defender for App Service provides dedicated security analytics to help you identify potential threats to your App Service resources. By the end of this PoC, you should be able to determine the value of Microsoft Defender for AppService and the importance to have this level of threat detection to your workloads. I hope you got real value out of this article and make sure to check out more articles from our Defender for Cloud PoC series, which can be found on our official ASC Tech Community.
P.S. Subscribe to our Microsoft Defender for Cloud Newsletter to stay up to date on helpful tips and new releases and join our Tech Community where you can be one of the first to hear the latest Defender for Cloud news, announcements and get your questions answered by Azure Security experts.
Reviewers:
@Yuri Diogenes, Principal PM Manager
@Tomer Spivak, Senior PM
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.