- Home
- Security, Compliance, and Identity
- Microsoft Sentinel Blog
- What’s New: Azure Sentinel Threat Intelligence Workbook
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Customers exploring threat intelligence indicators in their cloud workloads today face challenges understanding, aggregating, and actioning data across multiple sources. Threat intelligence is an advanced cybersecurity discipline requiring detailed knowledge of identifying and responding to an attacker based on observation of indicators in various stages of the attack cycle. Azure Sentinel is a cloud native SIEM solution that allows customers to import threat intelligence data from various places such as paid threat feeds, open-source feeds, and threat intelligence sharing communities. Azure Sentinel supports open-source standards to bring in feeds from Threat Intelligence Platforms (TIPs) across STIX & TAXII. Microsoft has released the next evolution of threat hunting capabilities in the Azure Sentinel Threat Intelligence Workbook.
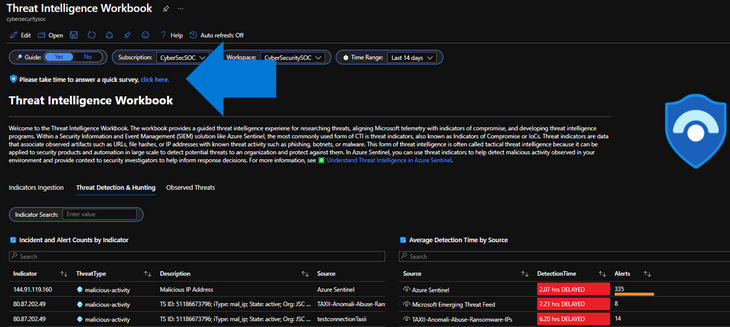
Azure Sentinel Threat Intelligence is based in ingestion of threat indicators such as IP addresses, domains, URLs, email senders, and file hashes. This provides a starting point for building threat intelligence programs which require the ability to both ingest and correlate threat data across cloud workloads. This offering provides a free text search to hunt for IPs, hash, emails etc. across 50+ Microsoft telemetry components. There are advanced correlations for AI/ML, UEBA, and geospatial location of threat sources.
Use Cases
There are several use cases for the Azure Sentinel Threat Intelligence Workbook depending on user roles and requirements. Common use cases include threat hunting, developing alerting, identifying security weaknesses, conducting assessments with custom reporting, time filtering, subscription filtering, workspace filtering, and guides. The workbook is organized into three sections:
- Indicators Ingestion: Evaluate indicators onboarded, threat feeds, and confidence ratings.
- Threat Detection & Hunting: Free text search indicators across your cloud workloads.
- Observed Threats: Analyze threats by geolocation, threat group, assets targeted and more.
Benefits
- Ingest, analyze, hunt for indicators within workloads
- Free text search to hunt for IPs, hash, emails etc. across 50+ Microsoft telemetry components
- Advanced correlations for AI/ML, UEBA, and geospatial location of threats
- Find, fix, resolve workload weaknesses
- Query/Alert generation
Visualization
- Dozens of visualizations, recommendations, queries
- Single-click report exports
Audience
- Threat Intelligence Professionals: Investigations
- SecOps: Alert/Automation building
- Assessors: Audit & assessment
- Security Decision Makers: Situational awareness
- MSSP: Consultants, Managed Service Providers
Getting Started
This content provides the capability to both ingest and correlate threat data in cloud workloads. The Threat Intelligence workbook provides a free text search to hunt for IPs, hashes, emails etc. across 50+ Microsoft telemetry components. There are advanced correlations for AI/ML, UEBA, and geospatial location of threat sources.
- Onboard Azure Sentinel
- Connect Threat Intelligence Platforms
- Connect STIX/TAXII Feeds
- Access the content
- Azure Sentinel > Threat Intelligence > Threat Intelligence Workbook
- Review the content and provide feedback through our survey
Frequently Asked Questions
- Why is Threat Intelligence needed?
- Correlate Cyber Threat Intelligence Indicators (CTI) observed in your workloads
- What types of indicators of compromise are included?
- Is Multi-Subscription & Multi-Tenant supported?
- Yes, via Workbook Parameters and Azure Lighthouse
- Is custom reporting available?
- Yes, via guide, time, workspace, & subscription parameters.
- Is 3rd Party integration supported?
- Yes, via Azure Sentinel Information Model (ASIM) integration.
- Is this available in government regions?
- Yes, Azure Sentinel Threat Intelligence is Generally Available in Commercial/Government regions
- Can this content be exported as a report?
- Yes, via Print Workbooks and Download Artifacts features.
- Is STIX/TAXI Integrated?
- Yes, the content scales via Connectors which populate in the ThreatIntelligenceIndicator data table.
- What is Dynamic Display?
- Dozens of queries are executed and only panels with data display
- What rights are required to use this content?
- Azure Sentinel Contributor can, create and edit workbooks, analytics rules, and other Azure Sentinel resources. Azure Sentinel Reader can view data, incidents, workbooks, and other Azure Sentinel resources.
Learn More About Threat Intelligence with Microsoft Security
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.