
Phishing campaigns continue to focus on social media, ramping up efforts to target users for the third consecutive year as the medium becomes increasingly used worldwide for communication, news, and entertainment.
The targeting of social media is the highlighted finding in the 2021 Phishing report by cybersecurity firm Vade, who analyzed phishing attack patterns that unfolded throughout 2021.
As part of their report, Vade analyzed 184,977 phishing pages to create stats based on billion corporate and consumer mailboxes that the cybersecurity firm protects.
Vade also recorded a rise in the sophistication of phishing attacks, especially those targeting Microsoft 365 credentials, an evolution in the tech support scams, and the inevitable dominance of COVID-19 and item shipping lures.
Social media takes the crown
In the top twenty most impersonated brands in phishing attacks, Facebook is in the first place, pushing Microsoft down to the second place.
WhatsApp also attained a respectable fourth place, ranking better than the previous year, while LinkedIn also made it to the top 20.
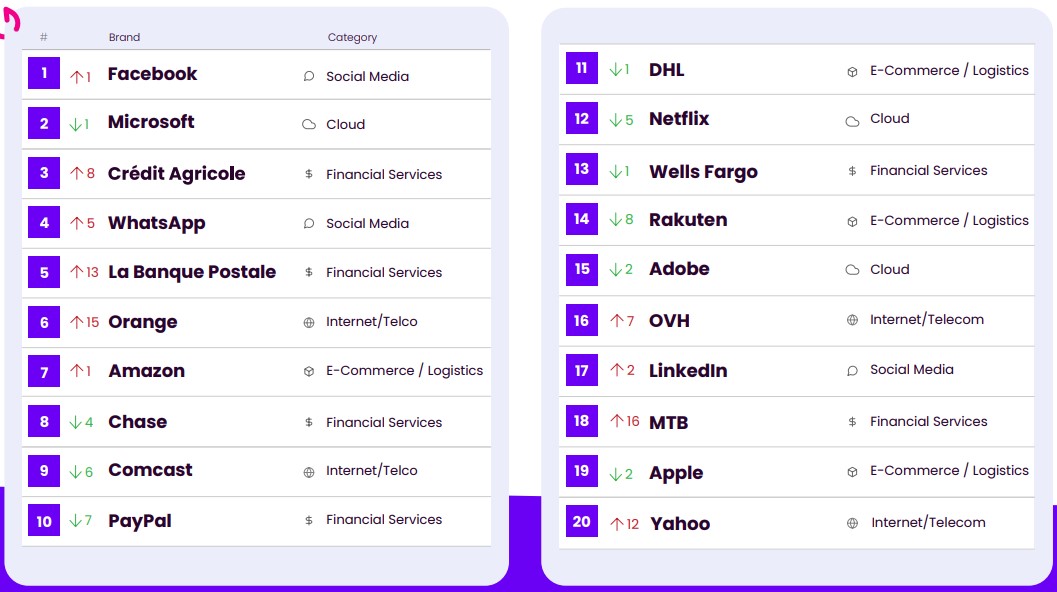
Phishing actors focused on Facebook (now Meta) and other social media platforms because taking over social media accounts is commonly a stepping stone to reach a wider audience or perform highly effective spear-phishing attacks.
In the first scenario, phishing actors can post links to malware-dropping or phishing sites that their followers, who trust them, are more likely to click on, thus generating traffic towards malicious sites. The more popular the compromised account is, the larger the targeted pool.
This is commonly seen on Twiter, where compromised “verified” accounts are used to promote crypto scams. For example, in 2020, high-profile verified Twitter accounts for Jeff Bezos, Kanye West, Bill Gates, Elon Musk, Apple, and many more were compromised to promote a fake cryptocurrency giveaway.
As Vade comments, the phishing actors are particularly interested in well-known brands and typically target them during periods of high recognition.
In the case of spear phishing, the actors may use access to compromised accounts to send direct messages to their friends and family and engage in high-level social engineering.
Even if the actors aren’t interested in abusing their access to social media accounts this way, they can always monetize the stolen credentials by extorting the victim or selling them to other threat actors.
Microsoft phishing
Among the most important other findings presented in Vade’s report is that phishing actors have raised their sophistication when targeting corporate users, going after their Microsoft 365 accounts.
“Vade detected a sophisticated Microsoft phishing attack in which corporate logos and background images were automatically rendered onto Microsoft 365 phishing pages,” details the report.
“Highly targeted, the attack was designed to trigger only if the email reached the intended victim, which the hacker validated by sending an API call to Microsoft with the victim’s email address.”
Once the victim’s identity is validated, the threat actors make an HTTP post request to fetch and load the target’s employer logo and background.
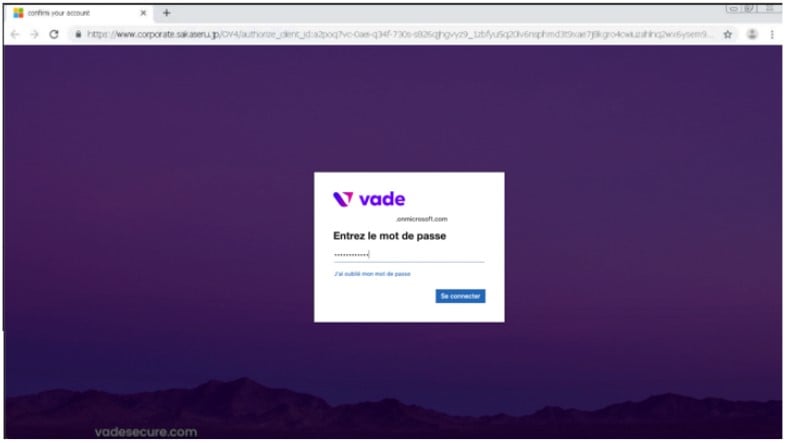
These dynamically-loading phishing pages are far more likely to trick victims into entering their Microsoft credentials than ordinary run-of-the-mill tactics.
The day matters
Statistical analysis shows that 78% of all phishing emails are sent during weekdays, while only 22% are kept for the weekend.
When the stats are isolated to Facebook phishing, Monday and Thursday appear to have the highest volume of phishing messages, while the weekend is the most serene time.
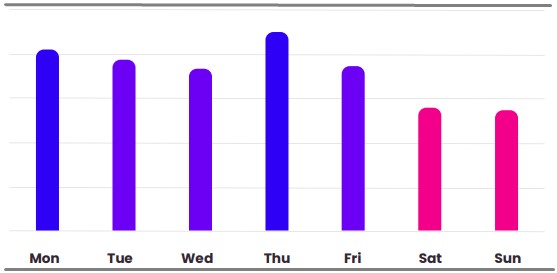
Possibly, the phishing actors have found that targets have more time and a clearer mind to identify signs of fraud during the weekend.
In Microsoft’s case, Vade saw a gradual rise in the number of phishing emails as the week progressed, possibly attempting to leverage accumulating tiredness that leads to carelessness and phishing link clicks.
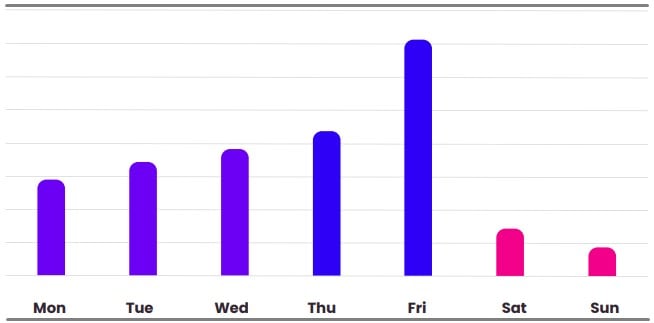
As expected, phishing campaigns targeting Microsoft accounts went almost totally silent during the weekend, as there can be no realistic corporate-level lures at this time.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now