
A new malware framework known as NetDooka has been discovered being distributed through the PrivateLoader pay-per-install (PPI) malware distribution service, allowing threat actors full access to an infected device.
This previously undocumented malware framework features a loader, a dropper, a protection driver, and a powerful RAT component that relies on a custom network communication protocol.
The first samples of NetDooka were discovered by researchers at TrendMicro, who warn that while the tool is still in an early development phase, it is already very capable.
The fact that it’s being distributed through the PrivateLoader malware distribution service reflects this potency, as its authors deemed the malware ready for large-scale deployment.
PrivateLoader deployment
The PrivateLoader PPI service was first spotted a year ago and analyzed by Intel471 in February 2022. In short, it’s a malware distribution platform that relies on SEO poisoning and laced files uploaded onto torrent sites.
It has been observed distributing a wide variety of malware, including Raccoon Stealer, Redline, Smokeloader, Vidar, Mars stealer, Trickbot, Danabot, Remcos, and various other malware strains.
TrendMicro analysts spotted NetDooka taking over control of the infection chain after being dropped on the victim’s machine in recent operations.
First, a loader is decrypted and executed, checking the Windows Registry for the existence of antivirus tools that will be removed or disabled.
Next, a malicious set of drivers is installed to act as kernel-mode protection for the RAT component, preventing the deletion of the payload or the termination of its processes.
Finally, the framework establishes a communications link to C2 for fetching the final payload, the NetDooka RAT. Trend Micro notes that in some cases, PrivateLoader drops the RAT directly.
.jpg)
NetDooka RAT
Before entering normal operation mode, NetDooka RAT checks if it’s running in an analysis environment and if a copy of itself already exists on the system.
The RAT receives commands via TCP and supports a range of functions like performing file actions, logging keystrokes, executing shell commands, using the host’s resources for DDoS attacks, or performing remote desktop operations.
The complete list of supported functions is given below:
- Exfiltrate system information
- Send session ID
- Send message
- Reverse shell
- DDoS attack
- Send file
- Download file
- Copy browser data
- Copy browser data
- Start HVNC
- Send log
- Microphone capture
- Start virtual network computing (VNC)
- Capture webcam
The communication between C2 and NetDooka RAT relies on a custom protocol, with the exchanged packets resembling the following format:
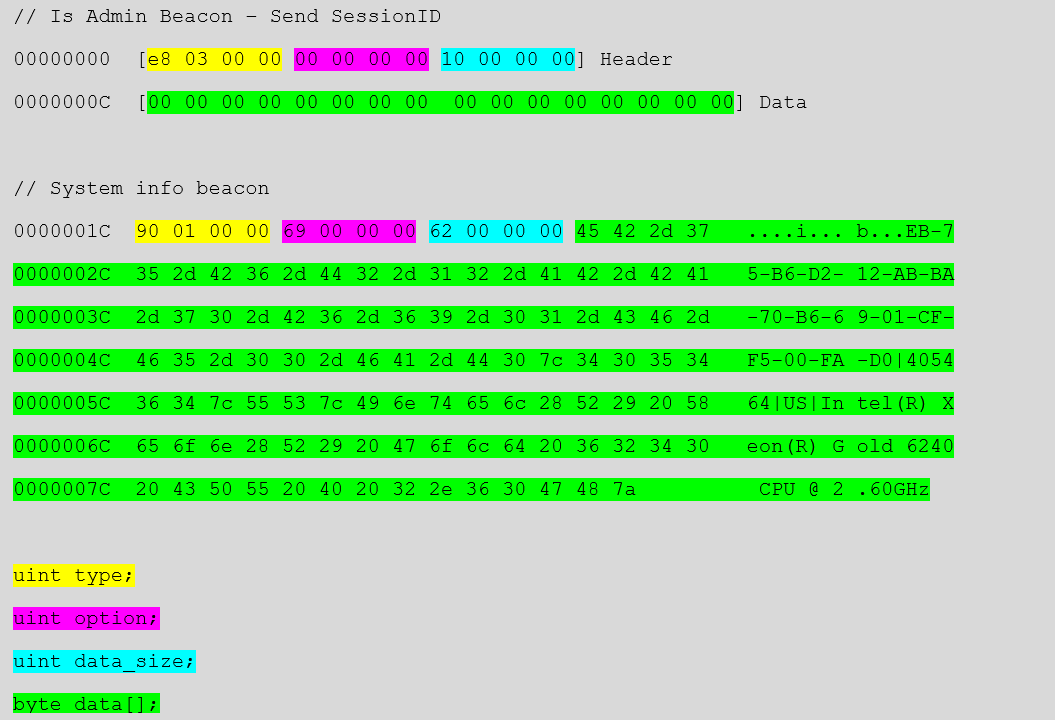
Because NetDooka is in an early development phase, any of the above may change soon, and there are already variants circulating that feature different function sets.
Right now, it’s a tool that threat actors could use to establish short-term persistence and perform information stealing and espionage operations.
However, since it incorporates a loader as part of the malware frame, it could fetch other malware strains besides its own RAT component.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now