The Quantum ransomware, a strain first discovered in August 2021, were seen carrying out speedy attacks that escalate quickly, leaving defenders little time to react.
The threat actors are using the IcedID malware as one of their initial access vectors, which deploys Cobalt Strike for remote access and leads to data theft and encryption using Quantum Locker.
The technical details of a Quantum ransomware attack were analyzed by security researchers at The DFIR Report, who says the attack lasted only 3 hours and 44 minutes from initial infection to the completion of encrypting devices.
Using IcedID as initial access
The attack seen by The DFIR Report used the IcedID malware as the initial access to the target's machine, which they believe arrived via a phishing email containing an ISO file attachment.
IcedID is a modular banking trojan used for the past five years, primarily for second-stage payload deployment, loaders, and ransomware.
The combination of IcedID and ISO archives has been used in other attacks recently, as these files are excellent for passing through email security controls.
Two hours after the initial infection, the threat actors inject Cobalt Strike into a C:\Windows\SysWOW64\cmd.exe process to evade detection.
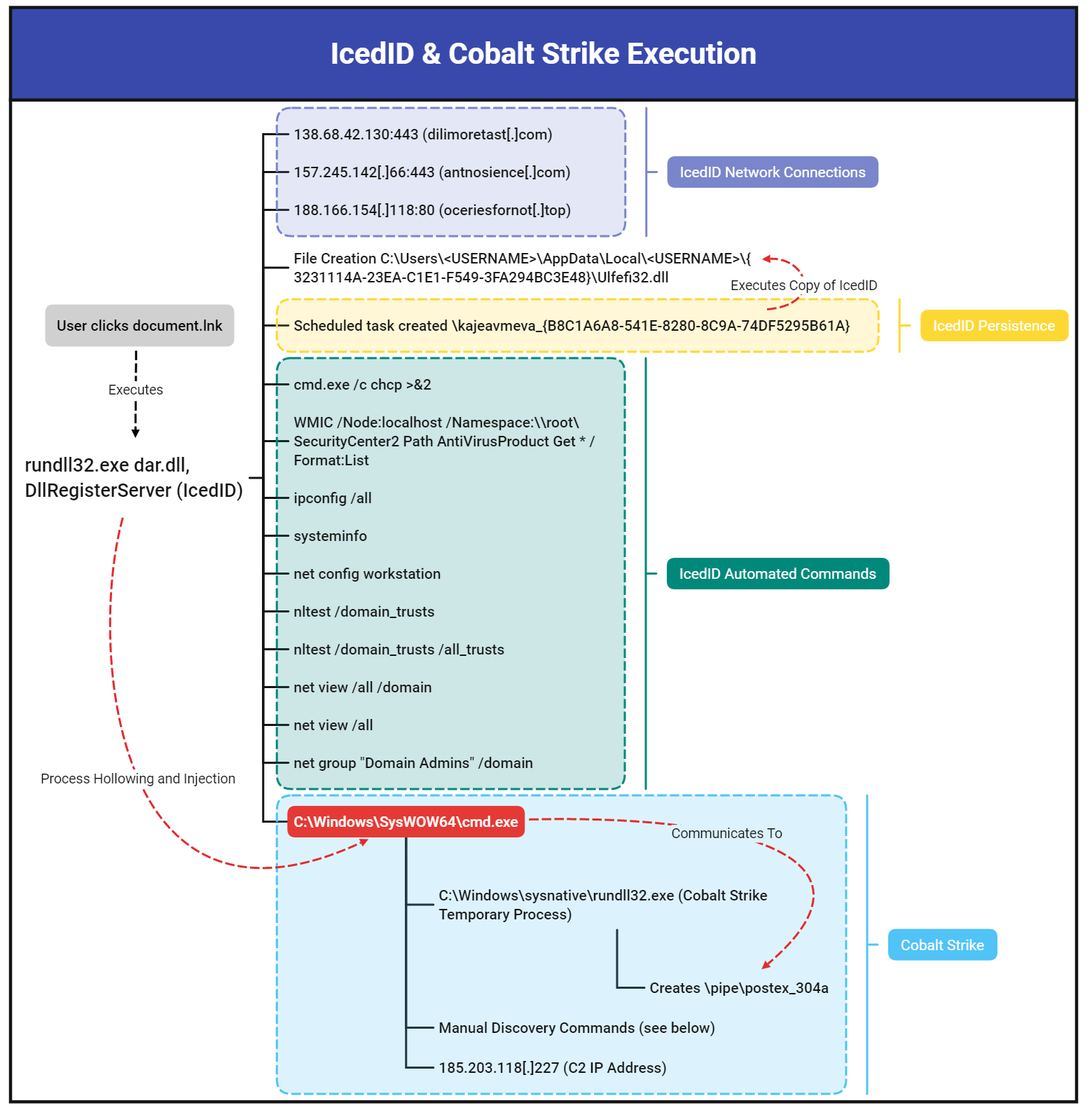
At this phase, the intruders stole Windows domain credentials by dumping the memory of LSASS, which allowed them to spread laterally through the network.
"For the next hour, the threat actor proceeded to make RDP connections to other servers in the environment," details The DFIR Report in the technical analysis.
"Once the threat actor had a handle on the layout of the domain, they prepared to deploy the ransomware by copying the ransomware (named ttsel.exe) to each host through the C$ share folder."
Eventually, the threat actors used WMI and PsExec to deploy the Quantum ransomware payload and encrypt devices.
This attack only took four hours, which is quite fast, and as these attacks commonly occur late at night or over the weekend, it does not provide a large window for network and security admins to detect and respond to the attack.
For more details about the TTPs used by Quantum Locker, The DFIR Report has provided an extensive list of indicators of compromise as well as C2 addresses that IcedID and Cobalt Strike connected to for communication.
Who is Quantum Locker?
The Quantum Locker ransomware is a rebrand of the MountLocker ransomware operation, which launched in September 2020.
Since then, the ransomware gang has rebranded its operation to various names, including AstroLocker, XingLocker, and now in its current phase, Quantum Locker.
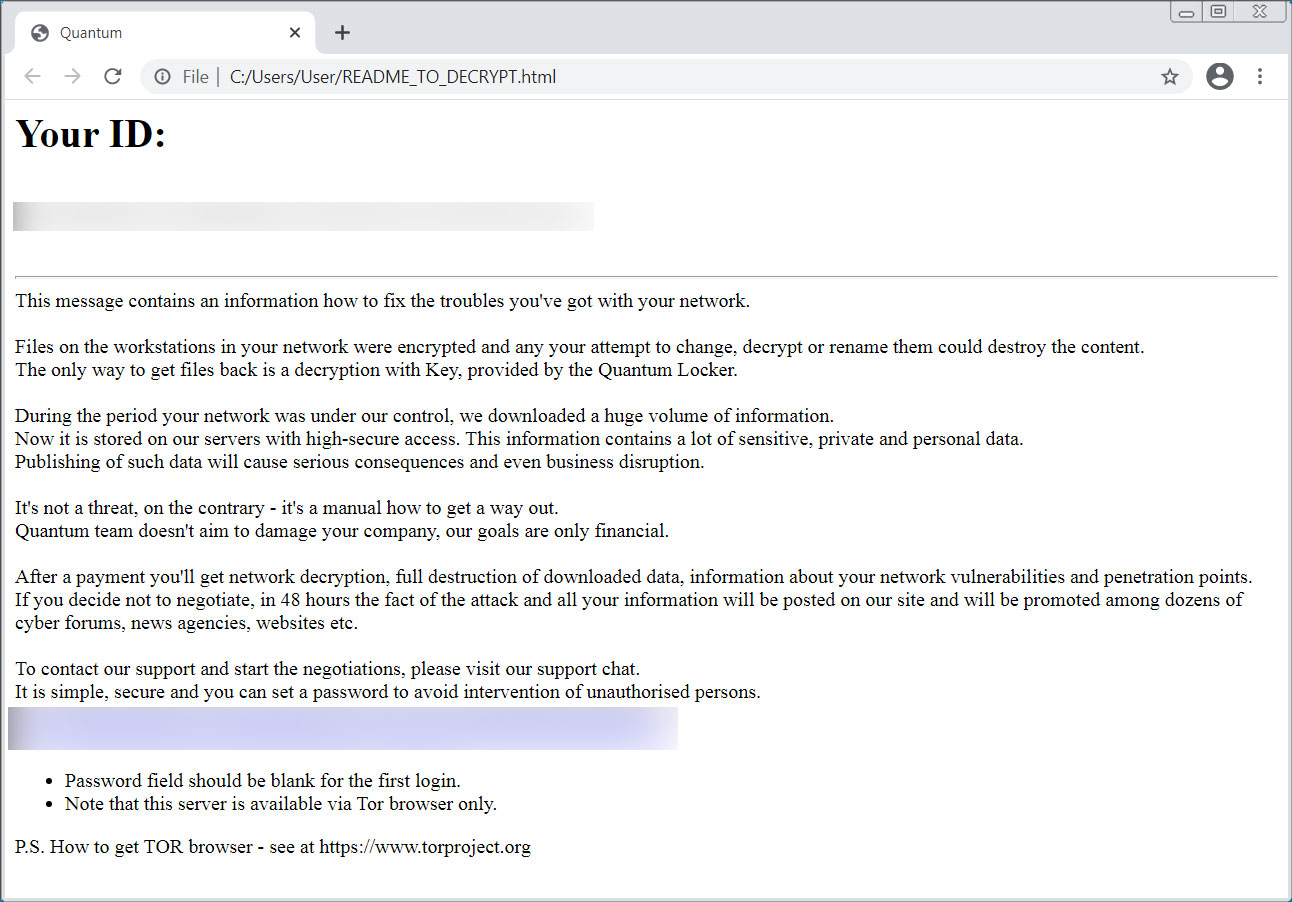
The rebrand to Quantum occurred in August 2021, when the ransomware encryptor began appending the .quantum file extension to encrypted file names and dropping ransom notes named README_TO_DECRYPT.html.
These notes include a link to a Tor ransom negotiation site and a unique ID associated with the victim. The ransom notes also state that data was stolen during the attack, which the attackers threaten to publish if a ransom is not paid.
Source: BleepingComputer
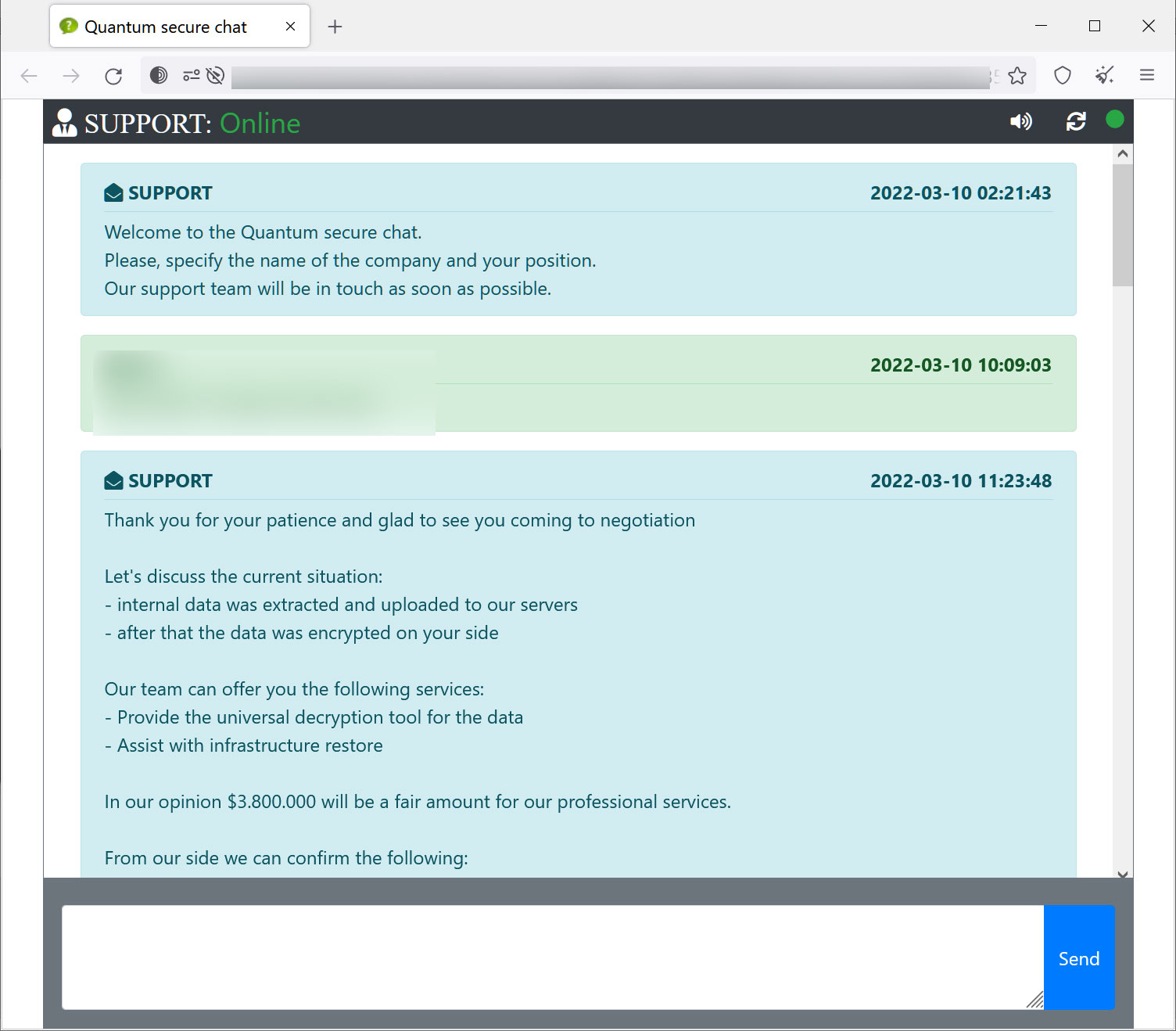
While The DFIR Report states that they saw no data exfiltration activity in the attack they analyzed, BleepingComputer has confirmed in the past that they do steal data during attacks and leak it in double-extortion schemes.
The ransom demands for this gang vary depending on the victim, with some attacks demanding $150,000 to receive a decryptor, while others seen by BleepingComputer are multi-million dollar demands, as shown below.
Source: BleepingComputer
Thankfully, Quantum Locker is not a very active operation like its previous incarnations, with only a handful of attacks each month.
However, while they may not be as active as other ransomware operations, such as Conti, LockBit, and AVOS, they are still a significant risk and it is important for network defenders to be aware of the TTPs related to their attacks.


Comments
PoliteDiplomacy - 1 year ago
there are some aspects worth questioning in this report.
among other things, the credentials theft. the hackers extracted domain admin credentials from lsass, that means the either process context was running as domain admin or some background process running as admin, terrible stuff either way. who runs their daily account as domain admin? either not probable, or a company asking for trouble. there are also good protections for credentials in memory, like running protected process, credential guard, attack surface reduction rules and so on. so this is another sign that the affected company was far from taking security seriously. also securing rdp, wmi from lateral movement are basic settings to implement in windows domain network. this report could also be called -how the customer did everything wrong.