
The non-fungible token (NFT) marketplace OpenSea is investigating a phishing attack that left 17 of its users without more than 250 NFTs worth around $2 million.
NFTs represent data stored on a blockchain, Ethereum in this case, that declares ownership of digital files, typically media files of artwork.
Currently valued at $13.3 billion and considered one of the largest in the world, OpenSea is a peer-to-peer NFT marketplace that also enables trading rare digital items and crypto collectibles.
Exploiting a migration
Phishing actors are always looking for ways to take advantage of changes that require users to take action and the OpenSea NFT theft is no different.
Researchers at Check Point say in a report today that the phishing actors knew about OpenSea upgrading its smart contract system to purge old and inactive listings on the platform and prepared for the migration with emails and websites of their own.
OpenSea informed its users that they had to update their listings between February 18 - 25 if they wanted to continue using the platform.
To help them in the process, the platform sent all users emails with instructions on how to confirm the migration of the listings.
The phishing actors took advantage of this process and used their own email addresses to send out the message from OpenSea to validated users, tricking them into thinking their original confirmation didn't go through.
The link embedded into the phony email pointed to a phishing website where victims were prompted to sign a transaction, supposedly concerning the migration.
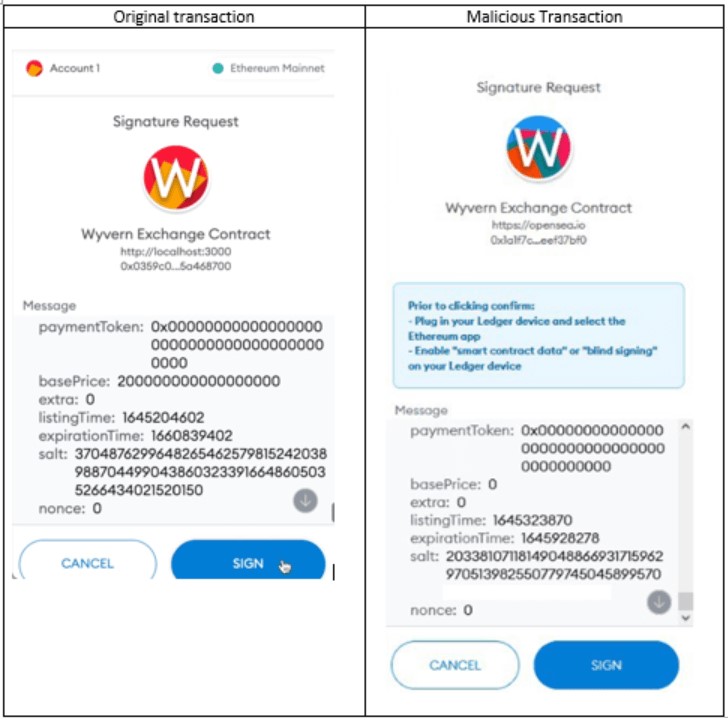
Instead, the transaction enabled the actor to perform a series of forwarding requests with verified parameters, resulting in passing the NFT ownership to the attacker.
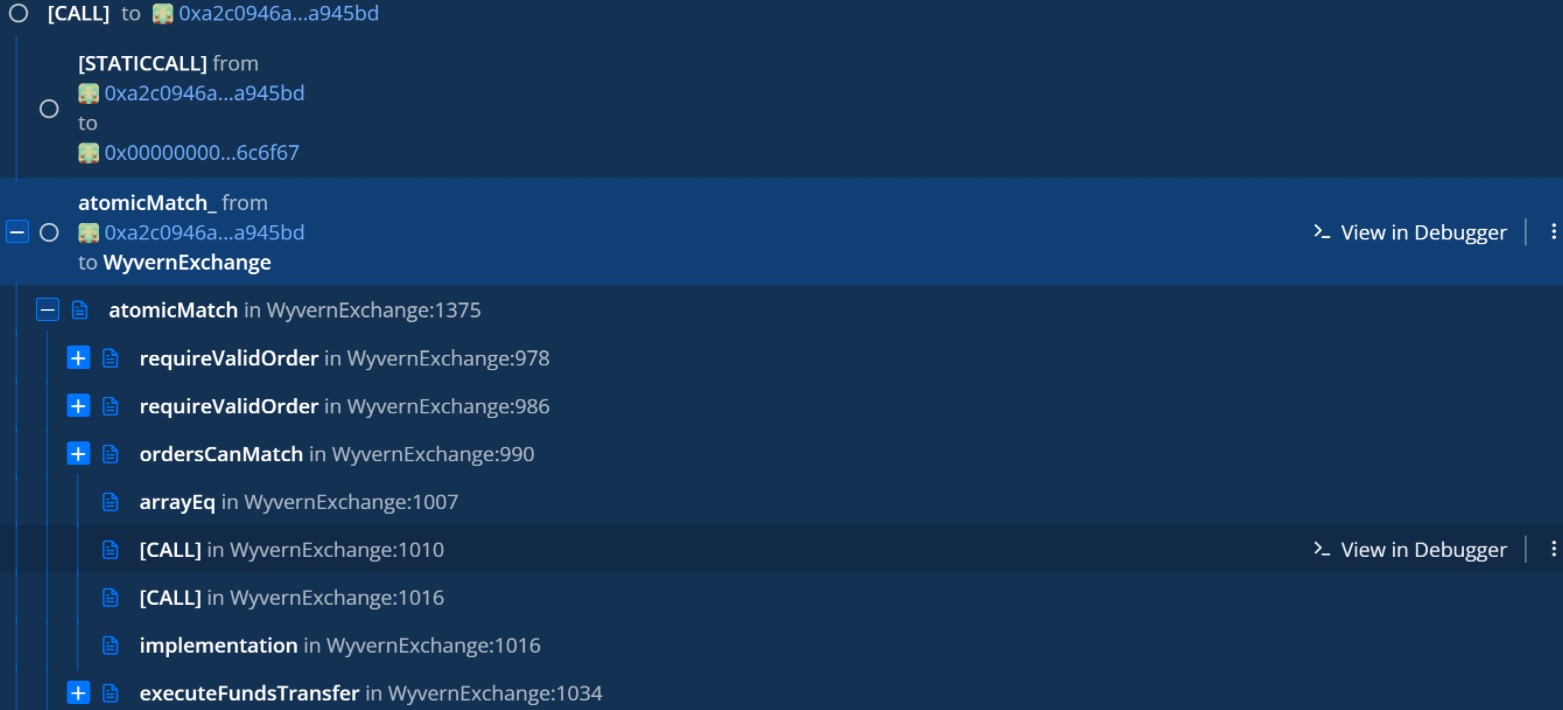
As Check Point explains, the actor even executed a dry run back on January 21, 2022, to verify that the attack would work as intended.
OpenSea not compromised
OpenSea was quick to point that the attack doesn't exploit any vulnerabilities on the platform or its trading systems, but instead relies solely on deceiving users through phishing.
As such, the platform has advised users to remain vigilant and avoid following any links that don't belong to the opensea.io domain.
Our team has been working around the clock to investigate the specific details of this phishing attack. While we haven’t yet determined the exact source, we wanted to share a couple of EOD updates:
— OpenSea (@opensea) February 21, 2022
Also, the phishing emails were confirmed to originate from outside the platform, confirming that the platform's email distribution system has not been compromised.
At this time, the attack appears to have stopped, the most recent transaction occurring yesterday.
Keep NFTs to yourself
Signing transactions without paying attention gives others permission to transfer ownership of your digital assets. Requests from the exchange platform excepted, all other transaction requests should be rejected.
If these requests come via emails, you should always verify the sender before taking any action. Ethereum offers a tool to check your token approvals and revoke them if needed.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now