
GitHub can now block and alert you of pull requests that introduce new dependencies impacted by known supply chain vulnerabilities.
This is achieved by adding the new Dependency Review GitHub Action to an existing workflow in one of your projects. You can do it through your repository's Actions tab under Security or straight from the GitHub Marketplace.
It works with the help of an API endpoint that will help you understand the security impact of dependency changes before adding them to your repository at every pull request.
"The GitHub Action automates finding and blocking vulnerabilities that are currently only displayed in the rich diff of a pull request," said Courtney Claessens, a Senior Product Manager at GitHub.
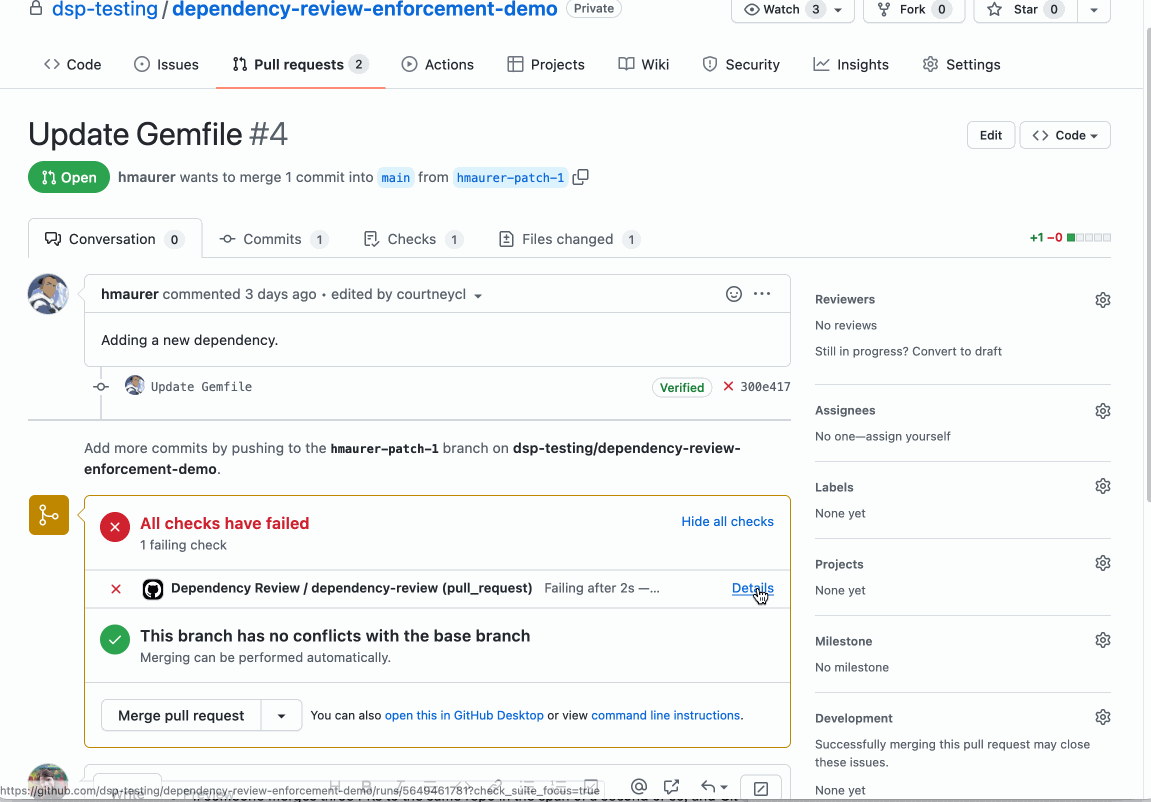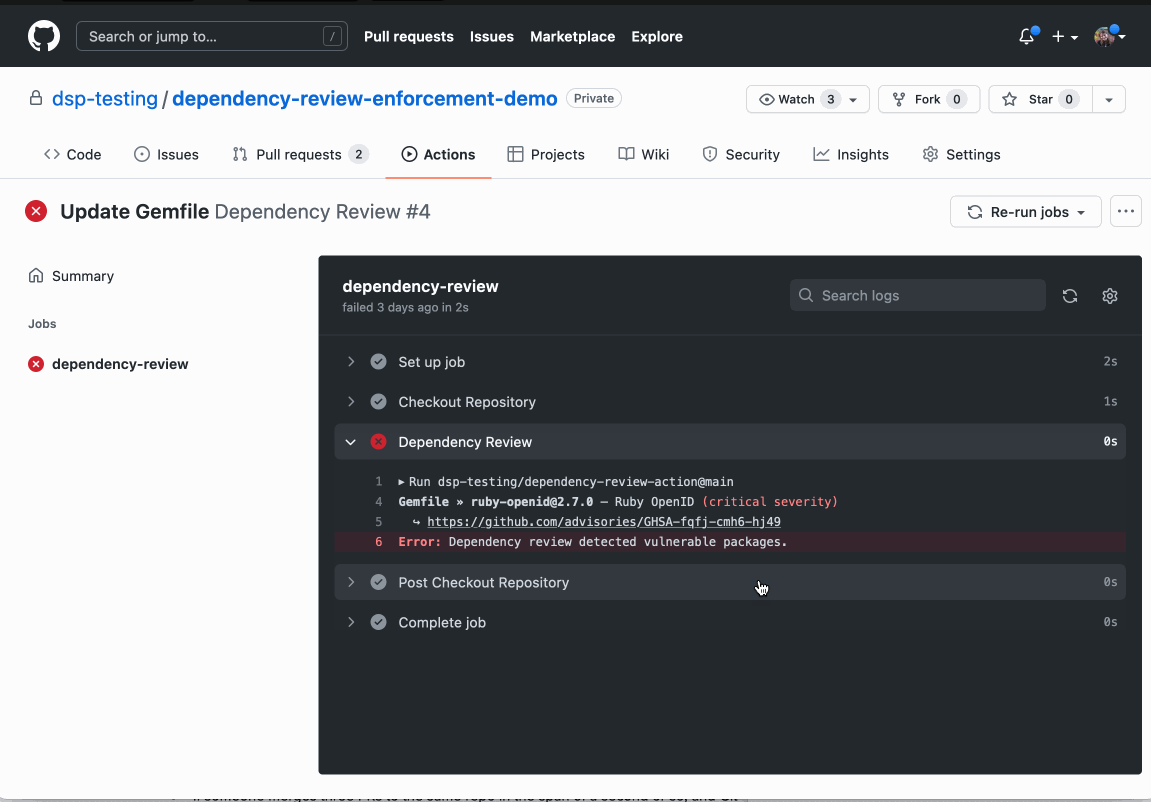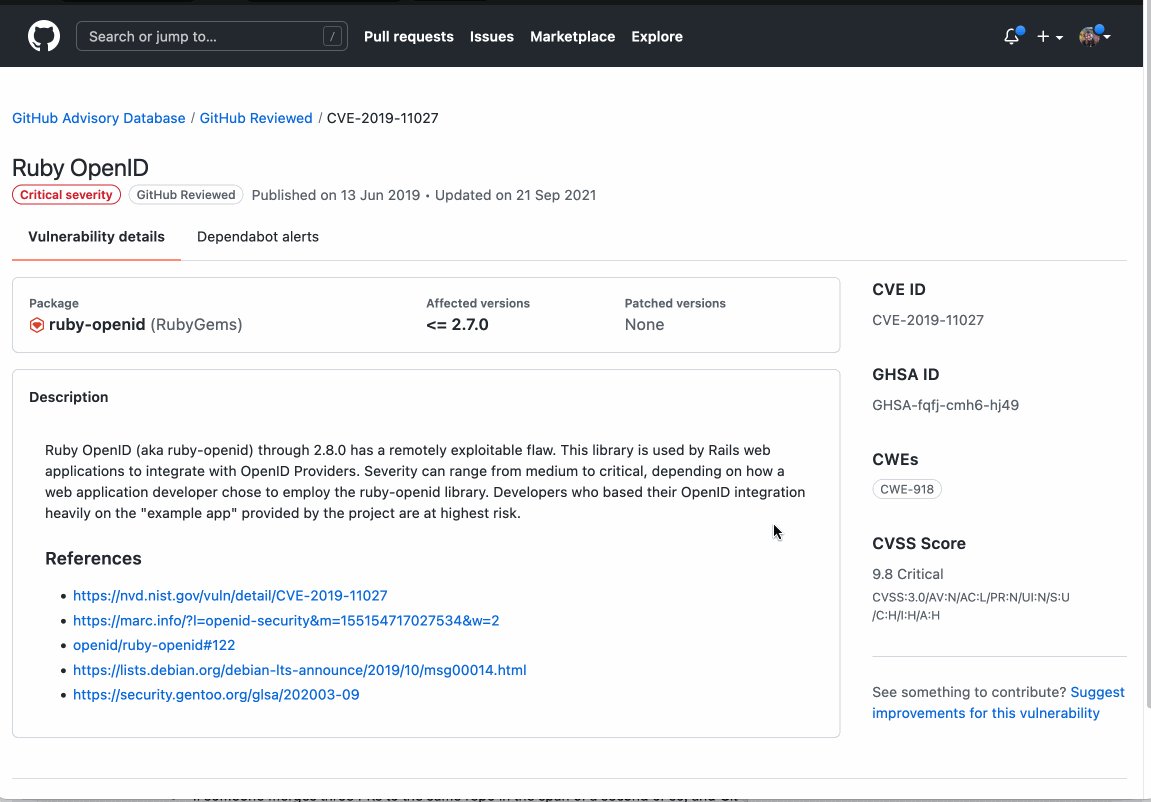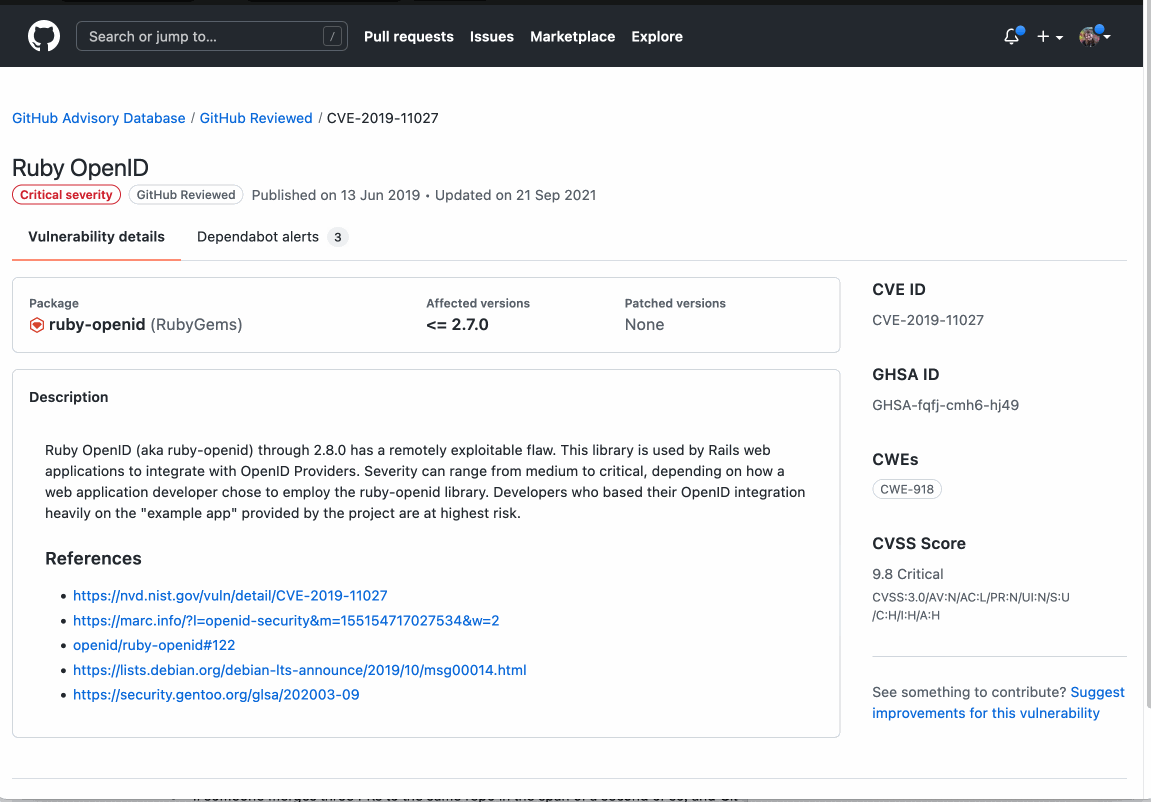
It works by scanning pull requests for dependency changes against the GitHub Advisory Database (a collection of CVEs and advisories detailing security flaws in open-source software) to see if new dependencies introduce vulnerabilities.
"If they do, the action will raise an error so that you can see which dependency has a vulnerability and implement the fix with the contextual intelligence provided," Claessens added.
Dependency review is designed to provide information on:
- Which dependencies were added, removed, or updated, along with the release dates
- How many projects use these components
- Vulnerability data for these dependencies
"By checking the dependency reviews in a pull request, and changing any dependencies that are flagged as vulnerable, you can avoid vulnerabilities being added to your project," GitHub explains.
"Dependabot alerts will find vulnerabilities that are already in your dependencies, but it's much better to avoid introducing potential problems than to fix problems at a later date."
The Dependency Review action is currently in public beta and is available for all public repositories and for private repositories belonging to organizations using GitHub Enterprise Cloud with a license for GitHub Advanced Security.
You can find more info on how Dependency Review works here. GitHub also provides detailed installation steps on the action's marketplace entry.
GitHub also announced on Monday that it extended its code hosting platform's secrets scanning capabilities for GitHub Advanced Security customers to prevent accidental exposure of credentials before committing code to remote repositories.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now