
Docker images with a download count of over 150,000 have been used to run distributed denial-of-service (DDoS) attacks against a dozen Russian and Belarusian websites managed by government, military, and news organizations.
Behind the incidents are believed to be pro-Ukrainian actors such as hacktivists, likely backed by the country's IT Army.
DDoS cyberattacks aim to cripple operations of by sending out more requests than the target can handle and becomes unavailable to legitimate clients.
Targeting Docker APIs
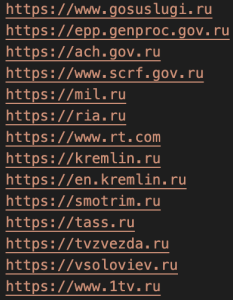
Among the 24 domains targeted include that of the Russian government, the Russian military, and Russian media like the TASS news agency.
Two Docker images involved in the attacks were spotted by threat researchers at cybersecurity company CrowdStrike, who observed them being deployed between February and March 2022.
Targeting exposed Docker APIs isn’t anything novel, as cryptocurrency mining gangs like Lemon_Duck and TeamTNT have been doing it for years.
Unfortunately, there’s a plethora of misconfigured or poorly secured Docker deployments out there, allowing threat actors to hijack the available resources for their purposes.
CrowdStrike noticed that its honeypots with exposed Docker Engine APIs were infected by two malicious images fetched straight from the Docker Hub repository.
The images are named “erikmnkl/stoppropaganda” and “abagayev/stop-russia”, and have been downloaded 50,000 times and 100,000 respectively. The numbers don’t necessarily reflect the volume of compromised hosts, which remains unclear at this time.
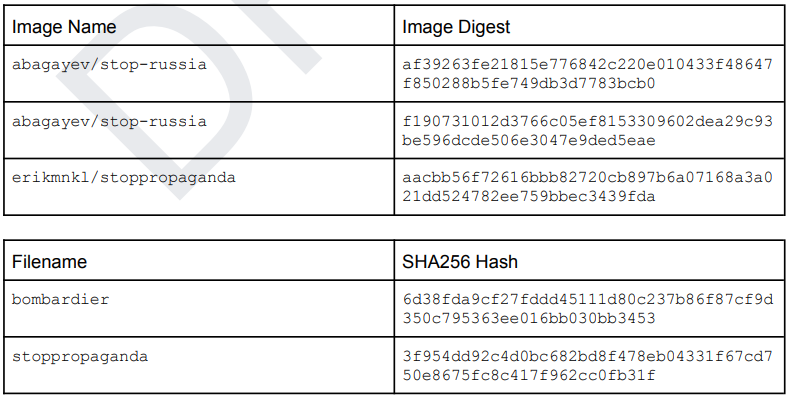
“The Docker image contains a Go-based HTTP benchmarking tool named bombardier with SHA256 hash 6d38fda9cf27fddd45111d80c237b86f87cf9d350c795363ee016bb030bb3453 that uses HTTP-based requests to stress-test a website. In this case, this tool was abused as a DoS tool that starts automatically when a new container based on the Docker image is created.” - CrowdStrike
The targets for the DDoS attacks were picked randomly at first but later versions of the images came with a time-based selection and a hardcoded list of targets, which were hit in one-hour assaults.
(CrowdStrike)
Due to the type of the operation and the targeting scope, CrowdStrike suggests that this campaign is very likely backed by the Ukraine IT Army or similar hacktivists.
Deploying these DDoS attacks may attract retaliatory action from pro-Russia hackers, which could lead to lengthy and damaging service disruption.
To help admins detect the unwanted activity, CrowdStrike has provided the following Snort rule:
.png)


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now