- Home
- Security, Compliance, and Identity
- Microsoft Defender for Endpoint Blog
- Defending Windows Server 2012 R2 and 2016
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Update: The modern, unified Microsoft Defender for Endpoint solution for Windows Server 2012 R2 and Windows Server 2016 is now generally available as of April 11th, 2022.
Ensure you apply the latest updates, including (after installing the MSI package) the new KB5005292 (update category: Microsoft Defender for Endpoint), so your machines receive the latest fixes and features.
In addition, Automated deployment and integration of the new solution with Microsoft Defender for Cloud is now available as the default solution with the new Microsoft Defender for Server P1 offering.
For automated deployment using Microsoft Endpoint Configuration Manager, this requires version 2207 or later.
Customers with machines on the existing Microsoft Defender for Server (now labeled P2) offering can either enable the new solution with a toggle, or target the MDE.Windows extension for deployment using the Microsoft Defender for Cloud initiative "Deploy Microsoft Defender for Endpoint agent on applicable images".
Introduction
In today's threat landscape protecting all your servers is critical, particularly with human-operated and sophisticated ransomware attacks becoming more prevalent. Our mission for endpoint protection is to cover all endpoints regardless of platform, clients, and servers, and inclusive of mobile, IoT and network devices.
Today, we are adding a broad set of prevention, detection and response capabilities, previously only available on Windows Server 2019 and later, to Microsoft Defender for Endpoint on Windows Server 2012R2 and 2016 using a modernized, completely revamped solution stack.
Introducing our modernized, unified solution for Windows Server 2012 R2 and 2016!
We are proud to introduce the public preview of a completely revamped Microsoft Defender for Endpoint solution stack for Windows Server 2012 R2 and Windows Server 2016. Whilst keeping up to date and upholding security hygiene is arguably still the best go-to when it comes to increasing resilience and reducing attack surface, we believe this modern, unified solution brings the best of the Microsoft Defender for Endpoint capabilities for prevention, detection, and response - in a single package.
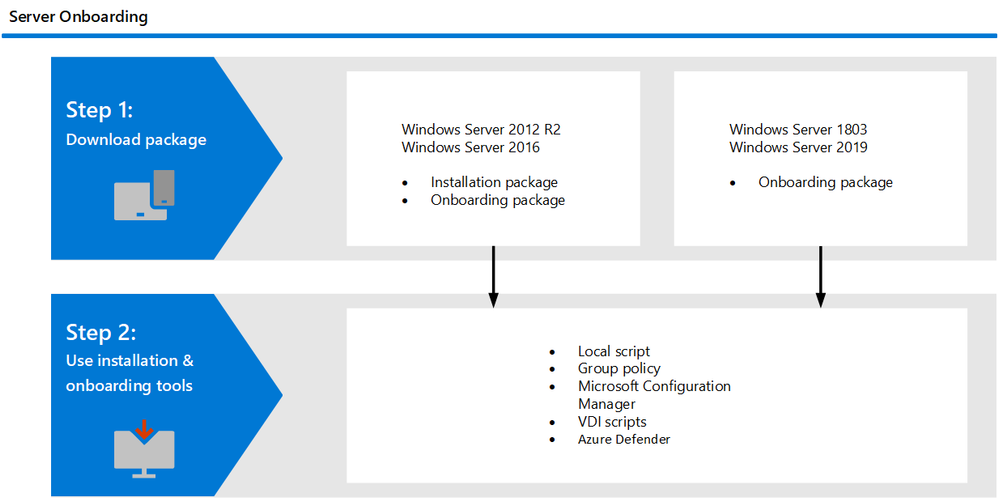
Server onboarding steps.
This new unified solution package reduces complexity by removing dependencies and installation steps. It also standardizes capabilities and functionality as it brings a very high level of parity with Microsoft Defender for Endpoint on Windows Server 2019:
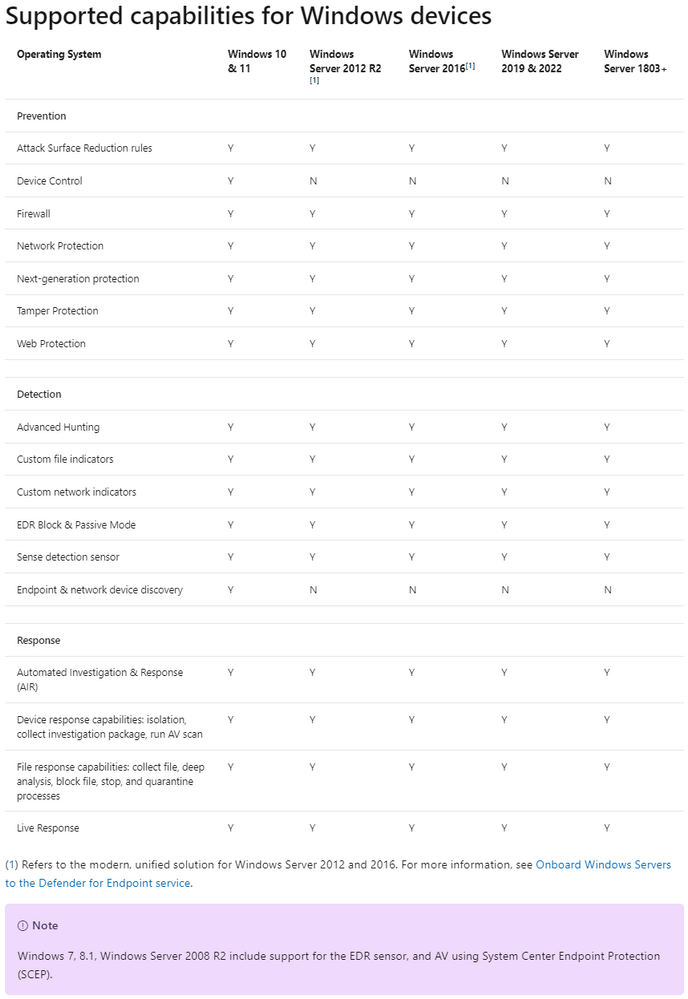
Overview of Microsoft Defender for Endpoint capabilities per operating system
Aside from having no specific client prerequisites or dependencies, the solution is functionally equivalent to Microsoft Defender for Endpoint on Windows Server 2019; meaning, all environment requirements around connectivity are the same and you can use the same Group Policy, PowerShell commands and Microsoft Endpoint Configuration Manager* to manage configuration. The solution does not use or require the installation of the Microsoft Monitoring Agent (MMA).
Depending on the server that you're onboarding, the unified solution installs Microsoft Defender Antivirus and/or the EDR sensor. The following table indicates what component is installed and what is built in by default (Windows Server 2019 added for comparison only):
Improving resiliency against human-operated ransomware attacks
To avoid security controls, we have often seen attackers leveraging machines with older operating systems inside our client’s environments. As such, the endpoint visibility required to detect and prevent modern-day ransomware attacks was at the center of many of our design decisions for this release.
Specifically, we modeled across the MITRE tactics which we felt provides the best chances of early alerting and emphasized capturing actionable telemetry across these. Some areas include:
- Initial Access: Servers are often the first point of entry for motivated attackers. The ability to monitor signs of entry via publicly facing, vulnerable services is critical.
- Credential Access: Servers often contain sensitive credentials in memory from Administrator maintenance or other activities. Enhanced memory protections help identify potential credential theft activities.
- Lateral Movement: Improved user logon activity allows better mapping of attempted movement across the network to or from Servers
- Defense Evasion: Improved hardening via tampering protection provides security controls the best chance of preventing Ransomware’s most harmful effects on high value assets, such as Servers.
Next steps
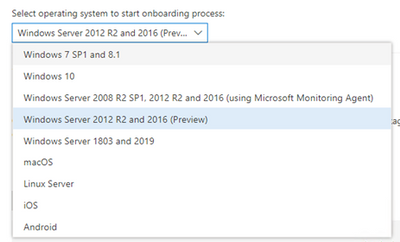
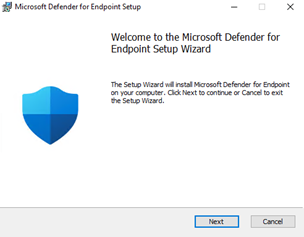
You can start testing today by simply visiting the Microsoft 365 Defender portal. If you have enabled preview features, you can download the installation and onboarding packages from the new onboarding page:
A screenshot of the new onboarding page option
A screenshot of the new installer
- Before installation, please ensure your machines are fully updated and continue to apply the latest component updates (including those for Defender Antivirus) containing important security improvements and bug fixes.
- For the EDR sensor on Windows Server 2012 R2 & 2016, we now have a new update package available: KB5005292. This update is only applicable after initial installation. Note that the latest update may already be included in the installer package you obtain from the onboarding page, as this package gets updated continuously.
- On Windows Server 2016, verify that Microsoft Defender Antivirus is installed, is active and up to date. You can download and install the latest platform version using Windows Update. Alternatively, download the update package manually from the Microsoft Update Catalog or from the Antimalware and cyber security portal .
- Ensure you meet all connectivity requirements; they match those for Windows Server 2019.
- You can now use the Group Policy templates for Windows Server 2019 to manage Defender on Windows Server 2012 R2 & 2016.
- Please take a look at New Windows Server 2012 R2 and 2016 functionality in the modern unified solution for known issues and limitations.
- Microsoft Endpoint Configuration Manager 2107 with the hotfix rollup or later is required to support configuration of the preview solution, including through Microsoft Endpoint Configuration Manager tenant attach. Fully automated deployment and onboarding will come in a later version*.
*If you have previously onboarded your servers using the Microsoft Monitoring Agent (MMA) either manually or though Microsoft Endpoint Configuration Manager, follow the guidance provided in Server migration for helpful steps to help you to migrate to the new solution.
- « Previous
-
- 1
- 2
- 3
- 4
- Next »
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.