
The stealthy BazarBackdoor malware is now being spread via website contact forms rather than typical phishing emails to evade detection by security software.
BazarBackdoor is a stealthy backdoor malware created by the TrickBot group and is now under development by the Conti ransomware operation. This malware provides threat actors remote access to an internal device that can be used as a launchpad for further lateral movement within a network.
The BazarBackdoor malware is usually spread through phishing emails that include malicious documents that download and install the malware.
However, as secure email gateways have become better at detecting these malware droppers, distributors are moving to new ways of spreading the malware.
Contact forms replacing emails
In a new report by Abnormal Security, analysts explain that a new distribution campaign started in December 2021 targets corporate victims with BazarBackdoor, with the likely goal of deploying Cobalt Strike or ransomware payloads.
Instead of sending phishing emails to the targets, the threat actors first use corporate contact forms to initiate communication.
For example, in one of the cases seen by Abnormal's analysts, the threat actors posed as employees at a Canadian construction company who submitted a request for a product supply quote.
After the employee responds to the phishing email, the attackers send back a malicious ISO file supposedly relevant to the negotiation.
Since sending these files directly is impossible or would trigger security alerts, the threat actors use file-sharing services like TransferNow and WeTransfer, as shown below.
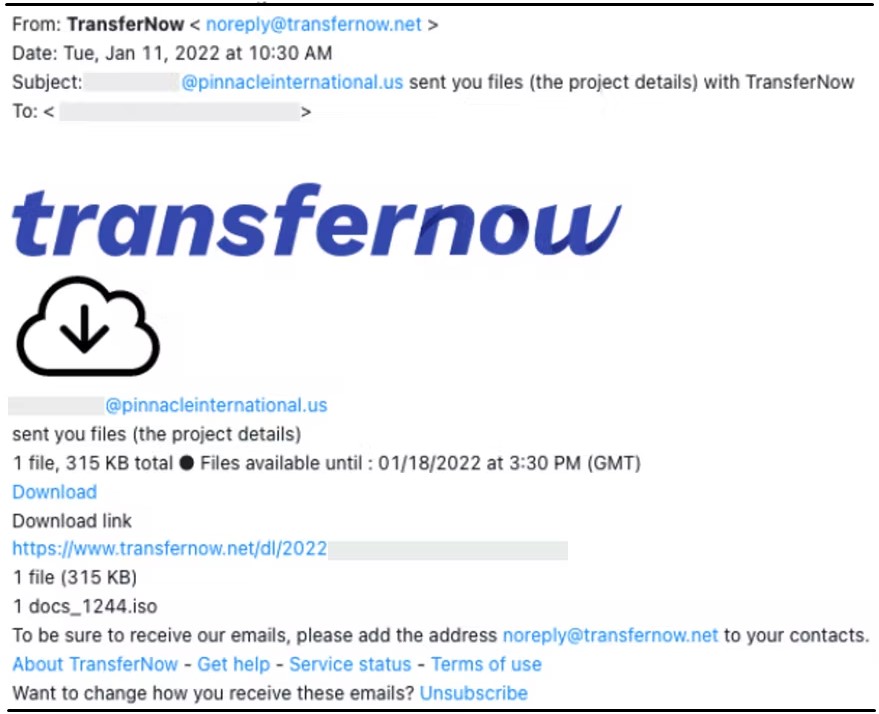
We reported a similar case of contact form abuse in August, where fake DMCA infringement notices sent via contact forms were installing BazarBackdoor.
In April 2021, we also reported on a phishing campaign using contact forms to spread the IcedID banking trojan and Cobalt Strike beacons.
Hiding BazarLoader
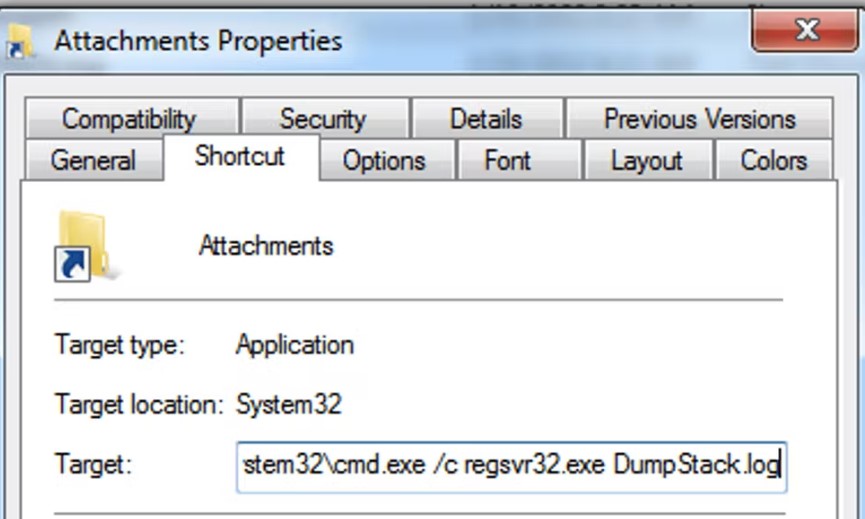
The ISO archive attachment contains a .lnk file and a .log file. The idea here is to evade AV detection by packing the payloads in the archive and having the user manually extract them after download.
The .lnk file contains a command instruction that opens a terminal window using existing Windows binaries and loads the .log file, which is, in reality, a BazarBackdoor DLL.
When the backdoor is loaded, it will be injected into the svchost.exe process and contact the command and control (C2) server to receive commands to execute.
Due to many of the C2 IPs being offline at the time of Abnormal's analysis, the researchers couldn't retrieve the second-stage payload, so the ultimate goal of this campaign remains unknown.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now