
Automotive parts manufacturer DENSO has confirmed that it suffered a cyberattack on March 10th after a new Pandora ransomware operation began leaking data allegedly stolen during the attack.
DENSO is one of the world's largest automotive components manufacturers, supplying brands such as Toyota, Mercedes-Benz, Ford, Honda, Volvo, Fiat, and General Motors with a wide range of electrical, electronic, powertrain control, and various other specialized parts.
The company operates out of Japan but has over 200 subsidiaries and 168,391 employees worldwide and reports $44.6 billion in revenue for 2021.
DENSO hit by Pandora ransomware gang
DENSO confirmed this weekend that their corporate network in Germany was breached on March 10th, 2022, in a statement shared with BleepingComputer.
The company claims it had detected the illegal access and responded immediately to cut off the intruder from the rest of the network devices, limiting the impact to the German division only.
"DENSO has confirmed that its group company in Germany network was illegally accessed by a third party on March 10, 2022," reads the press statement published by DENSO.
"After the detecting the unauthorized access, DENSO promptly cut off the network connection of devices that received unauthorized access and confirmed that there is no impact on other DENSO facilities."
All production plants and facilities continue to operate normally, so no supply chain disruption is expected from this security incident.
A disruption in the supply chain of DENSO would cause a domino effect in the production of cars on multiple facilities globally, hitting an industry that’s already struggling due to chip shortages and the closure of Ukraine-based plants.
While DENSO states that the cyberattack has not caused an impact on their operations, the new Pandora ransomware gang has begun leaking 1.4TB of files allegedly stolen during the network breach.
.jpg)
Samples of the leaked data seen by Bleeping Computer include purchase orders, technical schematics, non-disclosure agreements, etc. At this point, we cannot verify if the leaked files were stolen in the recent incident.
DENSO has informed the local investigative authorities of the breach, so if the circulated files are authentic, copying, sharing, or publishing them would constitute a violation of the firm’s intellectual property rights.
While Pandora is a ransomware gang with their own encryptor, it is unknown if they successfully encrypted files on DENSO's network before the attack was detected.
A security researcher claimed to have seen a network access listing on a dark web market a few months back and warned DENSO about the stolen credentials.
Funny enough, couple months ago I warned DENSO of threat actor selling access to their network, if it's the very same way they entered their network I am gonna flip my table https://t.co/rf7g3Pcp6u
— Rad V. (@radvadva) March 13, 2022
Even though the purchase of an initial access offering is a possible scenario, the company has not disclosed how they were breached at this time.
The cyberattack on DENSO is the third in 2022 against an automaker or notable car parts producer.
In February, Toyota, the world’s largest carmaker, had to halt production on 14 of its Japanese facilities due to a catastrophic IT failure on one of its primary suppliers.
Last week, Bridgestone confirmed a late February ransomware attack for which the LockBit group had taken responsibility and told media that some of its South and North American operations suffered downtime as a result.
Who is Pandora ransomware?
Pandora ransomware is a new operation launched in March 2022 that targets corporate networks and steals data for double-extortion attacks.
Once they gain access to a network, the threat actors will spread laterally through a network while stealing unencrypted files to be used in extortion demands.
When encrypting a device, the ransomware will append the .pandora extension to encrypted files names, as shown below.
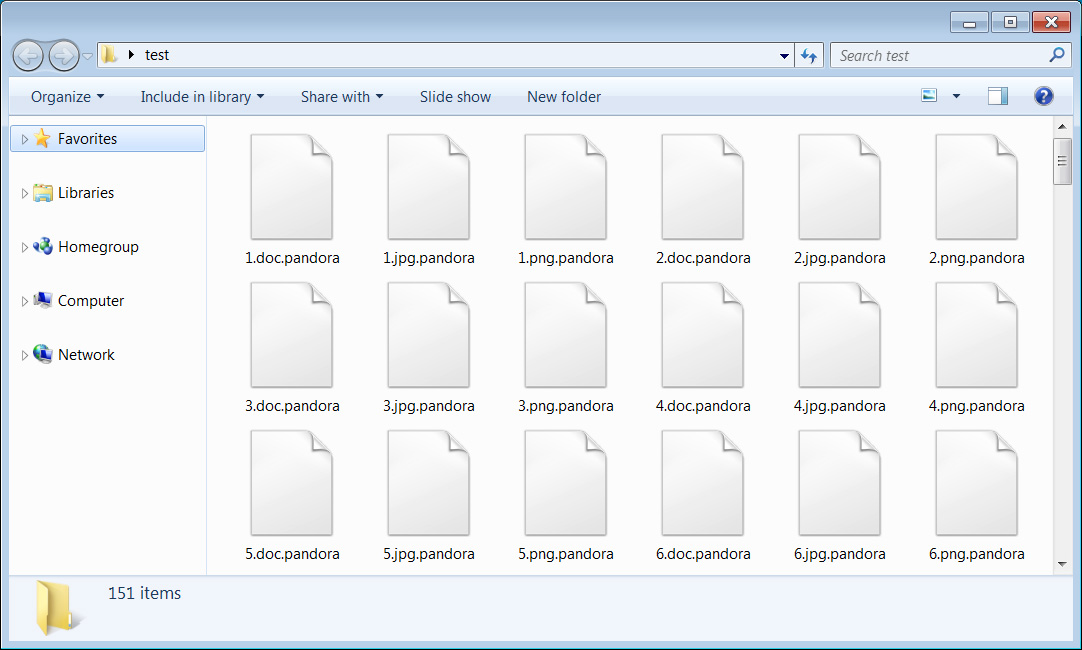
Source: BleepingComputer
As the ransomware encrypts files, Pandora will create ransom notes in every folder named 'Restore_My_Files.txt'. These ransom notes explain what happened to the device and include an email address that victims can contact to conduct ransom negotiations.
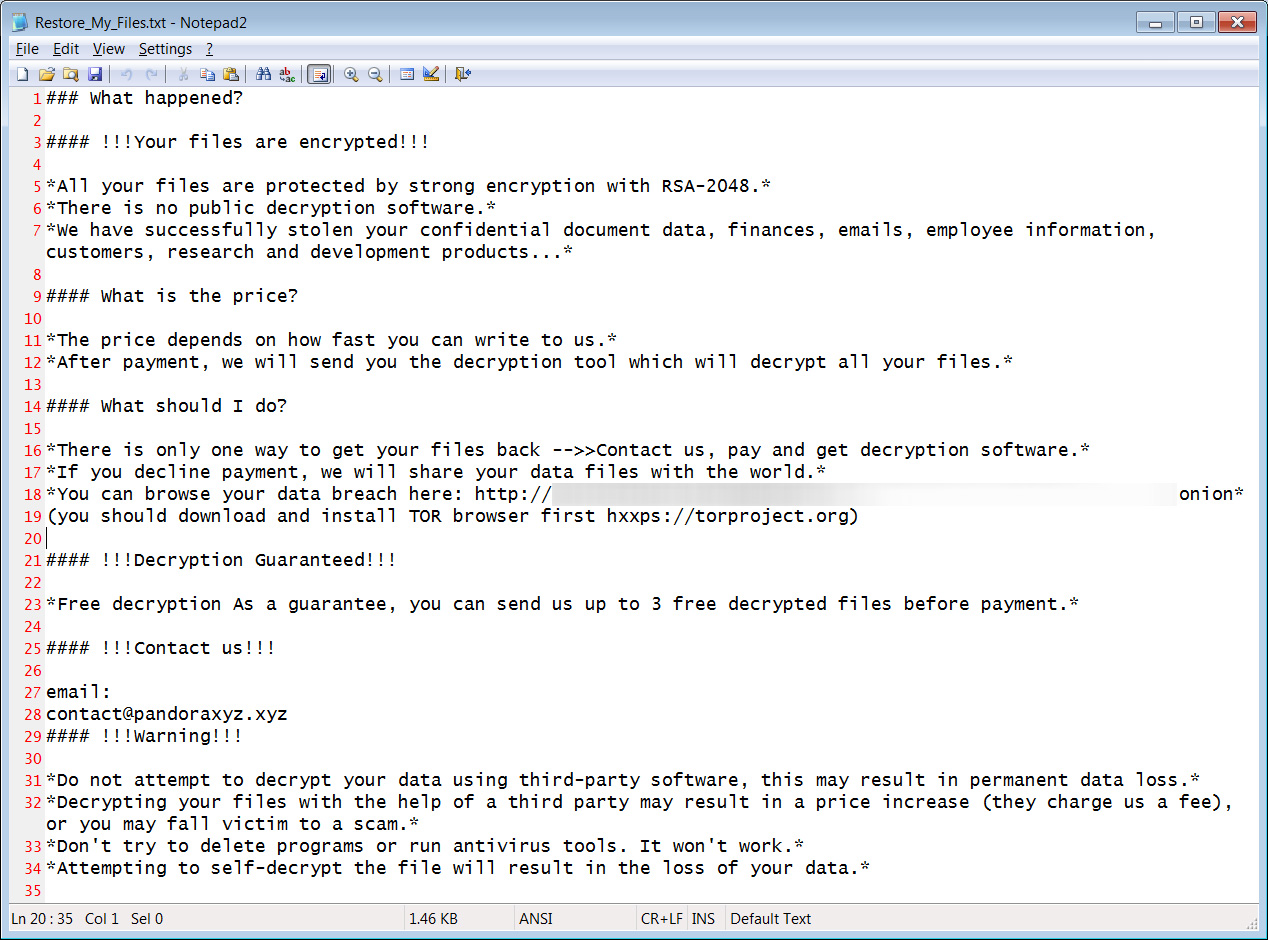
Source: BleepingComputer
The ransom notes also include a link to a data leak site used by the ransomware gang to conduct their double-extortion campaigns.
As the ransomware operation is very new, it is unknown how they gain access to corporate networks and how much they demand as a ransom.
Security researcher pancak3 believes that Pandora is a rebrand of the Rook ransomware due to code similarities and packers used by the operation.
A sample of the Pandora ransomware is detected on VirusTotal by Intezer as Rook, indicating code similarities.
Furthermore, security researcher Arkbird discovered that Pandora uses the same executable packer as 'NightSky,' a previous rebrand of the LockFile/AtomSilo ransomware operations.
(here Pandora vs Rook f87be226e26e873275bde549539f70210ffe5e3a129448ae807a319cbdcf7789) have similar process for unpack the implant to run. The final payload triggers also with the yara rules for the rook ransomware. So that an other renaming of Rook after NightSky. pic.twitter.com/i1wX9PEnaH
— Arkbird (@Arkbird_SOLG) March 14, 2022
Rook is also believed to be based off the source code from the Babuk ransomware operation, which was leaked on a hacker forum last September.
Strangely, Rook had also published data in December 2021 that allegedly belonged to DENSO, so it's not clear if the company was hit twice by the same ransomware operation.
Ransomware operations commonly rename themselves in what the security community calls a 'rebrand' in the hopes that it will help them evade law enforcement and potential sanctions from governments.
However, unless the threat actors completely change their malware's code, tools, and tactics, there will always be ways to detect when a gang rebrands, making it easier to link to previous ransomware operations.
If Pandora is a rebrand of Rook, we will likely see the operation running under this name for some time before it once again rebrands to another name, as we have previously seen with other versions of this ransomware family.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now