
Threat analysts have compiled a detailed technical report on FIN7 operations from late 2021 to early 2022, showing that the adversary continues to be very active, evolving, and trying new monetization methods.
FIN7 (a.k.a. Carbanak) is a Russian-speaking, financially motivated actor known for its resourceful and diverse set of tactics, custom-made malware, and stealthy backdoors.
Although some members of the group were indicted in 2018, followed by the sentencing of one of its managers in 2021, FIN7 did not disappear and kept developing new tools for stealthy attacks.
A rich new set of FIN7 indicators of compromise based on the analysis of novel malware samples has been published by researchers at Mandiant, who continue to observe and track the group’s operations.
The evidence gathered from a range of cyber-intrusions has led the analysts to merge eight previously suspected UNC groups into FIN7, which indicates the broad scope of operations for the particular group.
Evolution of toolset
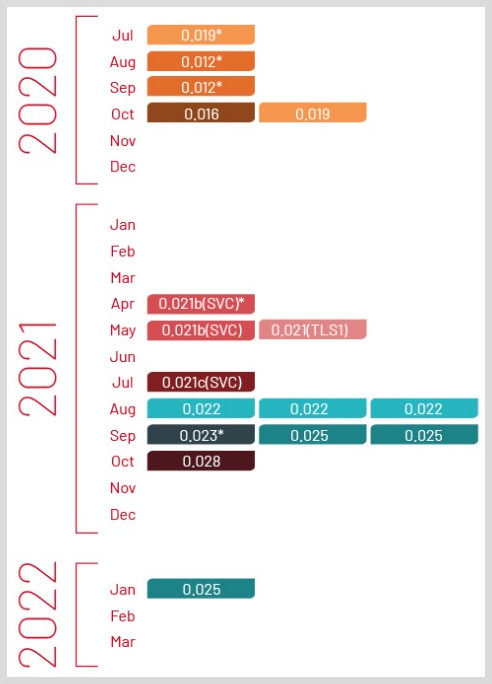
The PowerShell backdoor known as PowerPlant, which has been associated with FIN7 for years now, is still being developed into new variants, as Mandiant has identified version numbers ranging from 0.012 to 0.028.
In some intrusions, FIN7 was observed tweaking the functionality and adding new features to PowerPlant, and deploying the new version in the middle of the operation.
(Mandiant)
According to Mandiant, PowerPlant has replaced Loadout and Griffon in 2022 operations, while the Carbanak and Diceloader malware have also taken a back seat.
During deployment, PowerPlant fetches different modules from the C2 server, so the resulting set of capabilities varies. Two of the most commonly deployed modules are named Easylook and Boatlaunch.
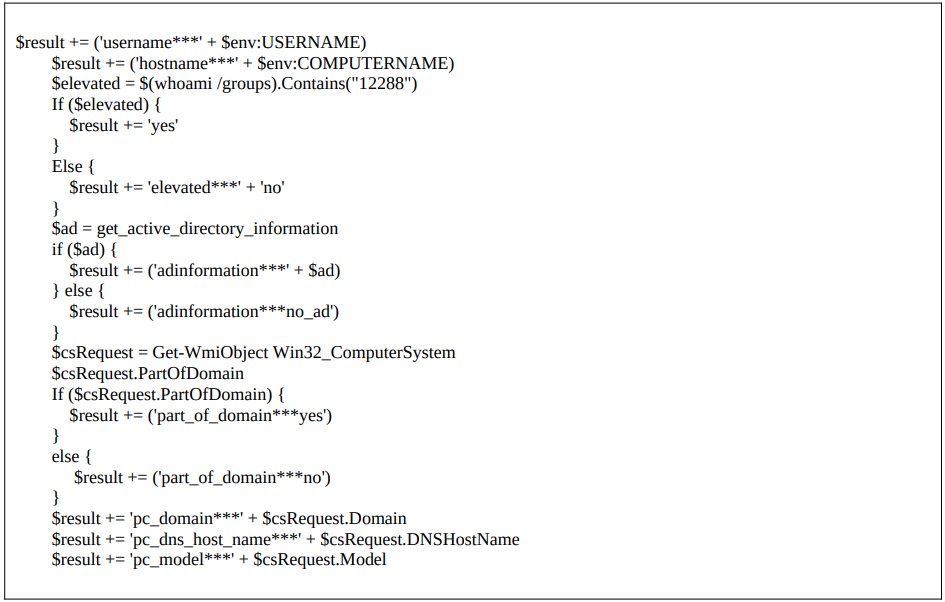
Easyloook is a reconnaissance utility that FIN7 has used for at least two years to capture network and system information details like hardware, usernames, registration keys, operating system versions, domain data, etc.
Boatlaunch is a helper module that patches PowerShell processes on the compromised systems with a 5-byte instruction sequence that results in an AMSI-bypass.
AMSI (antimalware scan interface) is a built-in Microsoft tool that helps detect malicious PowerShell execution, so Boatlaunch is there to help prevent that. Mandiant has spotted both 32-bit and 64-bit module versions.
Another new development is the evolution of the Birdwatch downloader, which has two variants now, named Crowview and Fowlgaze.
Both variants are .NET-based, but contrary to Birdwatch, they feature self-deletion capabilities, come with embedded payloads, and support additional arguments.
Like Birdwatch, these new variants support retrieving payloads over HTTP and continue to offer basic reconnaissance operations that tell FIN7 what processes run on the system, what the network configuration is, and what web browser is used.
New ventures in ransomware
One interesting finding presented in Mandiant’s report is FIN7's involvement with various ransomware gangs.
More specifically, the analysts have found evidence of FIN7 intrusions detected right before incidents with ransomware like Maze, Ryuk, Darkside, and BlackCat/ALPHV.
“In addition to evidence produced from intrusion data, secondary artifacts suggest FIN7 played a role in at least some DARKSIDE operations,” says Mandiant
“A low global prevalence code signing certificate used by FIN7 in 2021 to sign BEACON and BEAKDROP samples were also used to sign multiple unattributed DARKSIDE samples recovered in the wild.”

Last October, Bleeping Computer reported about FIN7’s rising interest in ransomware operations when the group was exposed for setting up a phony pentesting firm to hire network intrusion specialists.
Whether FIN7 offers initial network access to ransomware gangs or operate as affiliates and use the aforementioned strains is unclear. Still, there’s clear involvement of the adversary in ransomware operations.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now