
Security analysts warn of a sharp rise in API attacks over the past year, with most companies still following inadequate practices to tackle the problem.
More specifically, Salt Security reports a growth of 681% of API attack traffic in 2021, while the overall API traffic increased by 321%.
These stats underline that as industries adopt API solutions, attacks against them are growing disproportionally.
.jpg)
All data presented in Salt Security's report was taken from a survey of a diverse demographic of 250 employees working for companies of varied sizes.
API attacks
API (Application Programming Interface) is a software interface supporting online services that rely on connections to exchange data.
These connections need to be secured from unauthenticated access; otherwise, anyone would be able to snatch the content of the interactions between users and programs.
An API attack abuses API specifications to perform data breaches, DDoS, SQL injection, man-in-the-middle attacks, spread malware, or allow anyone to authenticate as a user.
The risks of these attacks are large-scale and dire, which is why 62% of respondents in Salt Security’s survey have delayed the deployment of applications due to API security concerns.
Taking the wrong approach
Salt Security pinpoints the problem is an over-reliance on pre-production API security and a focus on identifying security issues during the development phase.
Reality has shown that most API attacks exploit logic flaws that become evident only when the applications enter the runtime phase. However, just a quarter of companies still employs security teams at that final point.
Additionally, 34% of companies lack any API security strategy, so they rely solely on the vendor of the API solution.
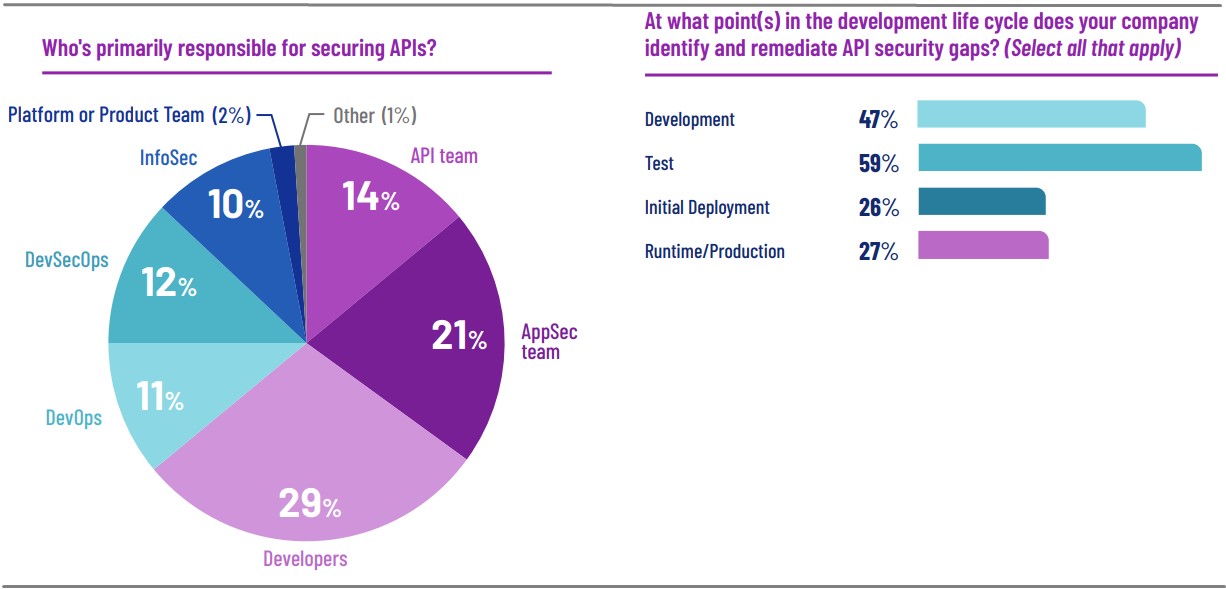
Finally, the data shows that deploying API gateways or WAFs is not enough to detect and stop XSS, SQL, and JSON injection attacks, as these are performed only after the threat actors have completed the necessary reconnaissance and identified usable security gaps.
Increasing complication
Most organizations require API updates and a certain feature enrichment after the initial employment, which creates an increasingly challenging project to manage.
Salt Security reports that 83% of its survey respondents lack confidence that their inventory and documentation reflect all existing API functions.
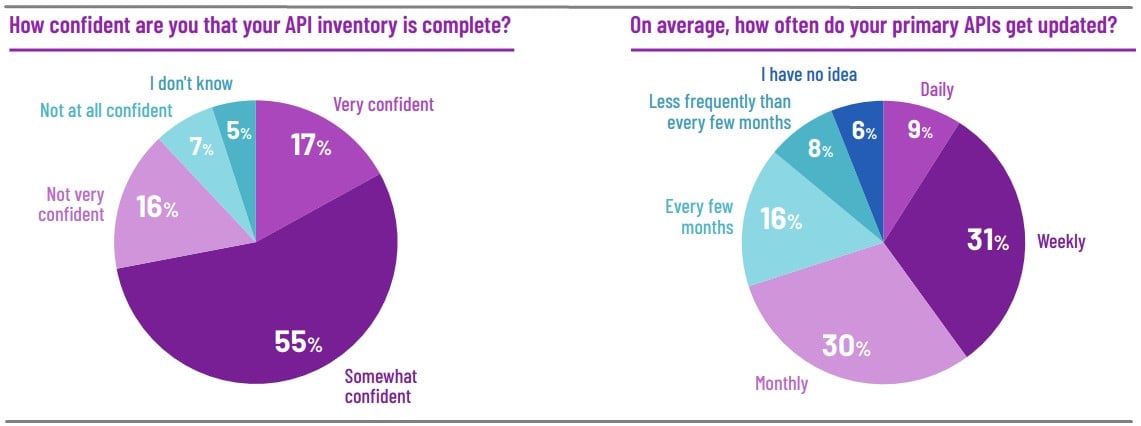
Another 43% reports concerns about outdated API functions that are no longer actively used in their apps but are still potentially available for abuse by threat actors.
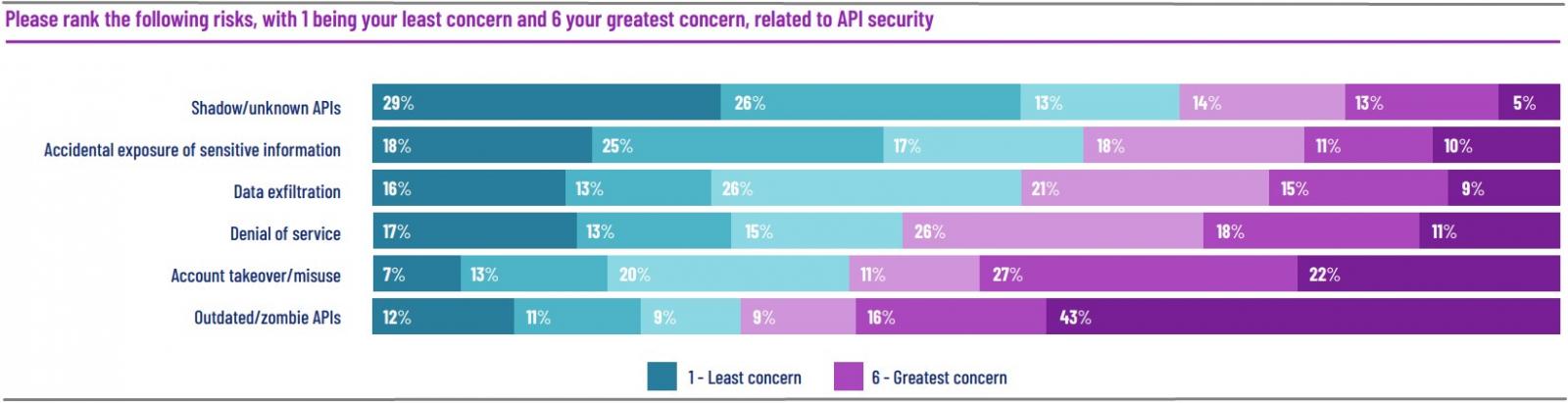
Security recommendations
Salt Security sees signs of a shift in how the industry perceives and handles API security but warns that we’re not there yet.
The main security recommendations given in the report are the following:
- Define a robust API security strategy for the entire lifecycle of APIs.
- Validate current API designs and existing controls and assess the current level of risk.
- Enable frictionless API security across all app environments, including on-premise, cloud, containers, legacy, etc.
- Use cloud data to identify patterns of malicious reconnaissance actions and stay one step ahead.
- Reduce your reliance on “shift-left” code review tactics, and invest more in runtime security.








Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now