
A small team of researchers at the Darmstadt University in Germany have published a report illustrating how their AirGuard app for Android provides better protection from stealthy AirTag stalking than other apps.
An Apple AirTag is a Bluetooth-based device finder released in April 2021 that allows owners to track the device using Apple's 'Find My' service.
Unfortunately, AirTags have great potential for abuse due to their small size as people can slip them into people's jackets, luggage, or even cars to track them without permission.
Although Apple has implemented an intricate anti-stalking system to prevent cases of abuse, stealthy AirTag tracking continues to remain a problem.
These features rely mainly upon identifying patterns of abuse, such as having an AirTag nearby that belongs to a different Apple account and serving warnings on the victim's iPhone.
Apple constantly updates this system with stricter rules and additions, but as hardware hackers have proved repeatedly, there are many ways to evade detection and disrupt the warning routines.
In the case of Android users, the problem is magnified because Apple left them without an official way to locate AirTags until December 2021, when it released Tracker Detect on the Play Store.
Tracker Detect, however, pales in comparison to its iOS counterpart, as it will only inform the victim they are tracked if it's commanded to perform a manual scan, and even then, it often misses nearby AirTags for no apparent reason.
A superior solution
The university researchers decided to do something about the Apple AirTag privacy problem in the Android world and reverse-engineered the iOS tracking detection to understand its inner workings better.
They then designed the AirGuard app, a fully automatic and passive detection anti-tracking solution that works against all Find My accessories and other tracking devices.
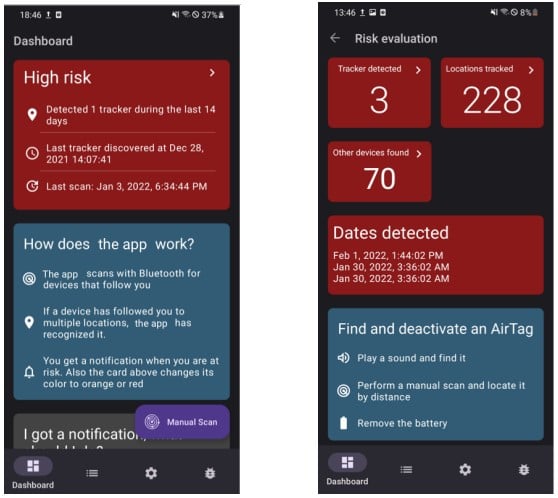
The app was released in August 2021, and since then, it has amassed a user base of 120,000 people. It can detect all Find My devices, including self-made ones like the cloned or modified AirTags, as the ultimate stealthy tracking tool.
The researchers have now published the results of their real-world tests taken from their experiments and drawn from community data of those using the app.
In summary, their approach was found to be superior to the iOS system, let alone Apple's own anti-tracking app for Android.
"The evaluation showed that AirGuard found more actual trackers in different scenarios compared to the iOS tracking detection," explained the researchers in a paper released this week.
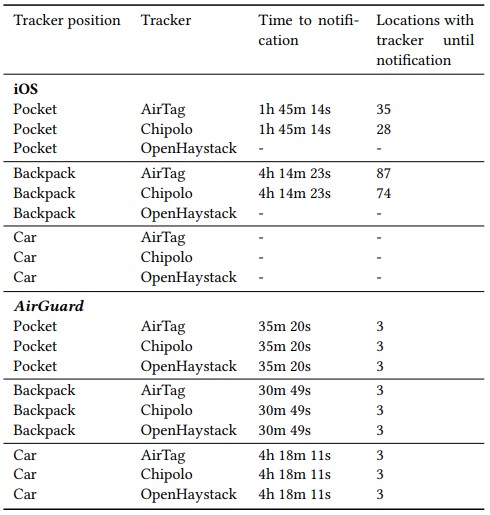
Apart from serving the tracking warnings faster, AirGuard can also detect trackers placed on cars, which is the most difficult for other solutions to unearth, and the best tracker placement option for malicious actors.
The only weakness of AirGuard against iOS is the limited scan opportunities granted by the Android OS, which makes the tracker location logs more sparing.
"As a comparison, iOS detected the AirTag at 35 locations in 1 h 45 min in the pocket scenario and AirGuard detected it at seven locations," further explained the researchers.
Should you use AirGuard?
The AirGuard app is open source software available for free via the Google Play Store, so its code is open to scrutiny, and the chances of the app being laced with malware are slim.
However, you should note that these apps request some risky permissions to function on your smartphone, which are integral to providing the promised service.
The detailed privacy policy that discloses precisely how AirGuard uses the collected user data can be found on this webpage.


Comments
brianm85temp - 2 years ago
The "risky" permissions are Bluetooth, location, and Internet access.
By that measure, just about any app is risky. If you can't trust the University that created this app, get a OnePlus phone and disable internet access to it. The app will still work.