
A rapidly growing botnet is ensnaring routers, DVRs, and servers across the Internet to target more than 100 victims every day in distributed denial-of-service (DDoS) attacks.
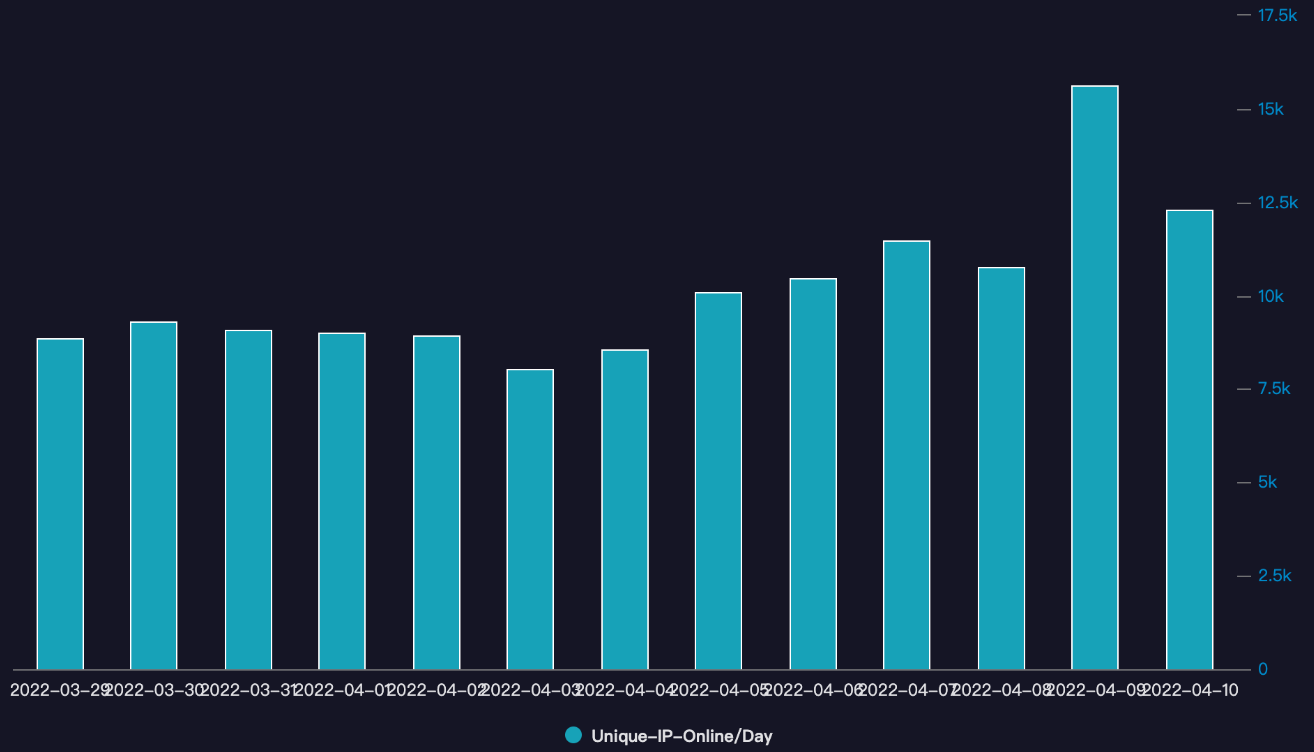
This newly discovered malware, named Fodcha by researchers at Qihoo 360's Network Security Research Lab (360 Netlab), has spread to over 62,000 devices between March 29 and April 10.
The number of unique IP addresses linked to the botnet also oscillates, with 360 Netlab saying that they're tracking a 10,000-strong Fodcha army of bots using Chinese IP addresses every day, most of them using the services of China Unicom (59.9%) and China Telecom (39.4%).
"Based on direct data from the security community that we worked with, the number of daily live bots are more than 56000," Netlab said.
"The global infection looks fairly big as just in China there are more than 10,000 daily active bots (IPs) and also more than 100 DDoS victims being targeted on a daily basis."
Spreads via exploits and brute-force attacks
The Fodcha infects new devices using exploits designed to abuse n-day vulnerabilities in multiple devices and a brute-force cracking tool dubbed Crazyfia.
The list of devices and services targeted by the Fodcha botnet includes but is not limited to:
- Android: Android ADB Debug Server RCE
- GitLab: CVE-2021-22205
- Realtek Jungle SDK: CVE-2021-35394
- MVPower DVR: JAWS Webserver unauthenticated shell command execution
- LILIN DVR: LILIN DVR RCE
- TOTOLINK Routers: TOTOLINK Routers Backdoor
- ZHONE Router: ZHONE Router Web RCE
Fodcha operators use Crazyfia scan results to deploy malware payload after successfully gaining access to vulnerable Internet-exposed devices samples on the vulnerable devices.
As 360 Netlab further discovered, the botnet samples target MIPS, MPSL, ARM, x86, and other CPU architectures.
Since January 2022, the botnet has been using the folded[.]in command-and-control (C2) domain up to March 19 when it switched to fridgexperts[.]cc after the cloud vendor took down the initial C2 domain.
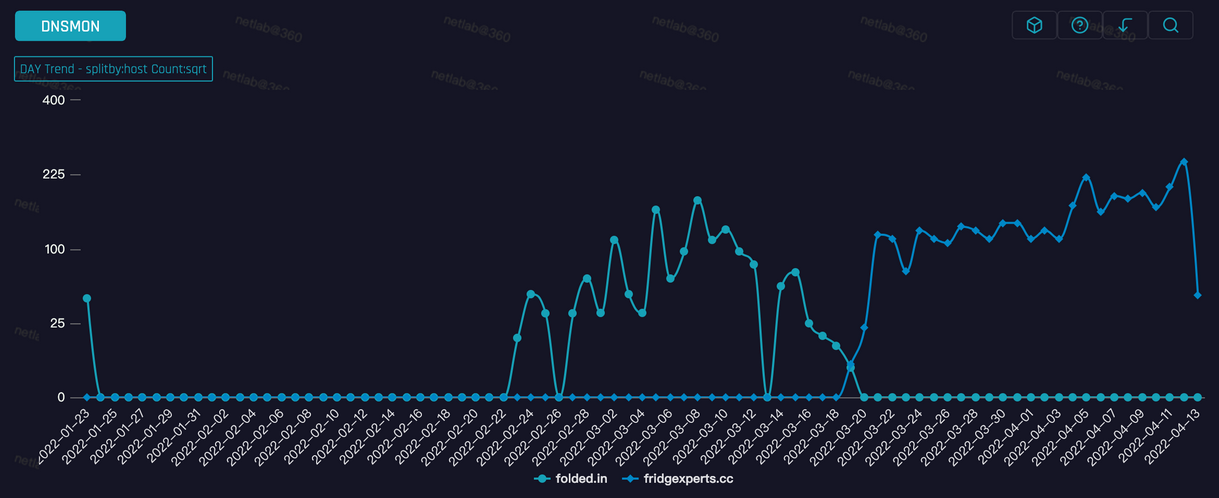
"The shift from v1 to v2 is due to the fact that the C2 servers corresponding to the v1 version were shutdown by a their cloud vendor, so Fodcha's operators had no choice but to re-launch v2 and update C2," the researchers concluded.
"The new C2 is mapped to more than a dozen IPs and is distributed across multiple countries including the US, Korea, Japan, and India, it involves more cloud providers such as Amazon, DediPath, DigitalOcean, Linode, and many others."
You can find further information on how the botnet works and indicators of compromise at the end of the 360 Netlab report.
Top 10 MITRE ATT&CK© Techniques Behind 93% of Attacks
Based on an analysis of 14M malicious actions, discover the top 10 MITRE ATT&CK techniques behind 93% of attacks and how to defend against them.











Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now