
A banking trojan for Android that researchers call Fakecalls comes with a powerful capability that enables it to take over calls to a bank’s customer support number and connect the victim directly with the cybercriminals operating the malware.
Disguised as a mobile app from a popular bank, Fakecalls displays all the marks of the entity it impersonates, including the official logo and the customer support number.
When the victim tries to call the bank, the malware breaks the connection and shows its call screen, which is almost indistinguishable from the real one.
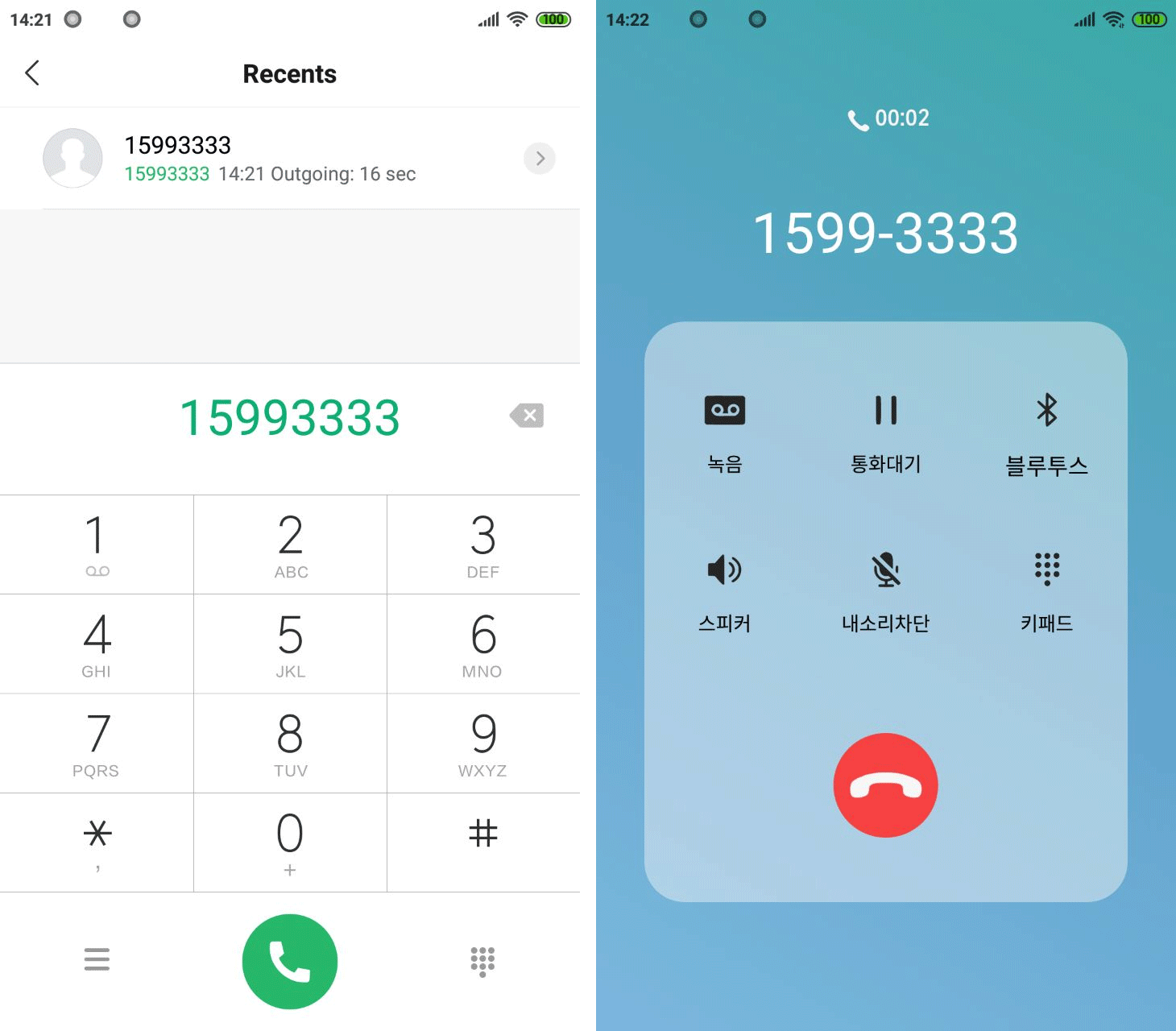
While the victim sees the bank’s real number on the screen, the connection is to the cybercriminals, who can pose as the bank’s customer support representatives and obtain details that would give them access to the victim’s funds.
Fakecalls mobile banking trojan can do this because at the moment of installation it asks for several permissions that give it access to the contact list, microphone, camera, geolocation, and call handling.
The malware emerged last year and has been seen targeting users in South Korea, customers of popular banks like KakaoBank or Kookmin Bank (KB), security researchers at Kaspersky note in a report today.
Although it’s been active for a while, the malware has received little attention - likely due to its limited target geography - despite its fake call feature that marks a new step in the development of mobile banking threats.
Direct line to threat actor
Kaspersky analyzed the malware and found that it can also play a pre-recorded message that mimics the ones typically used by banks to greet customers looking for support:
The malware developers recorded a few phrases that are commonly used by banks to let the customer know that an operator would take their call as soon as they become available.
Below are two examples of the pre-recorded audio (in Korean) that Fakecalls malware plays to make the ruse more realistic:
Hello. Thank you for calling KakaoBank. Our call center is currently receiving an unusually large volume of calls. A consultant will speak to you as soon as possible. <...> To improve the quality of the service, your conversation will be recorded.
Welcome to Kookmin Bank. Your conversation will be recorded. We will now connect you with an operator.
Kaspersky researchers say that the malware can also spoof incoming calls, allowing cybercriminals to contact victims as if they were the bank’s customer support service.
Complete spying kit
The permissions the malware requests upon installation allow the cybercriminals to spy on the victim by broadcasting in real-time audio and video from the device, see its location, copy files (contacts, files like photos and videos), and text message history.
“These permissions allow the malware not only to spy on the user but to control their device to a certain extent, giving the Trojan the ability to drop incoming calls and delete them from the history. This allows the scammers, among other things, to block and hide real calls from banks” - Kaspersky
While Fakecalls has been observed to support only the Korean language, which makes it easy to detect if the infected device runs with a different system language, the threat actor behind it could add more to extend to other regions.
Kaspersky’s recommendations to avoid falling victim to such malware include downloading apps only from official stores, and paying attention to potentially dangerous permissions an app asks for (access to calls, texts, accessibility), especially if the app does not need them.
Additionally, the researchers advise users to not share confidential information over the phone (login credentials, PIN, card security code, confirmation codes).


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now