
A YouTube influencer with hundreds of thousands of subscribers is encouraging followers to conduct cyber warfare against Russia.
In a plea made this week on his channel, the YouTuber demonstrated how viewers could download a free pen-testing (DDoS) tool called Liberator and "stop that Russian propaganda machine."
Albeit the cause might seem worthwhile and appealing, how legal is DDoS, and can users get in trouble?
YouTuber: 'I NEED YOUR HELP!'
In a YouTube video streamed Thursday, April 28th, a vlogger, Boxmining—who has over 268,000 subscribers, sought everyone's help in stopping Russian propaganda, amid the Kremlin's ongoing invasion of Ukraine.
The YouTube video in question has thus far generated over 86,000 views and counting at the time of writing.
"I need your help to support Ukraine! For the past few weeks, there have been numerous disinformation campaigns and fake news from the Russian government," says the YouTuber.
"These fake news flooded the media and had different effects around the globe."
"Very rarely do I ask people for help, but this is a situation where you can join the cyber warfare against Russia to stop that Russian propaganda machine," continued Boxmining.
Without wasting time, Boxmining quickly demonstrates how can you download an offensive security tool called 'Liberator' and partake in conducting cyber warfare against Russia using nothing other than your own computers and a VPN connection.
Created by the hacktivist group, 'disBalancer,' the Liberator app works by using your computer to attack Russian websites that spread misinformation related to current events.
Liberator conducts what is referred to as a Distributed Denial of Service (DDoS) attack.
A DDoS attack works by several machines (bots) repeatedly flooding servers of a website with excessive requests in a short span of time, such that the servers run out of their allotted bandwidth, and become unresponsive.
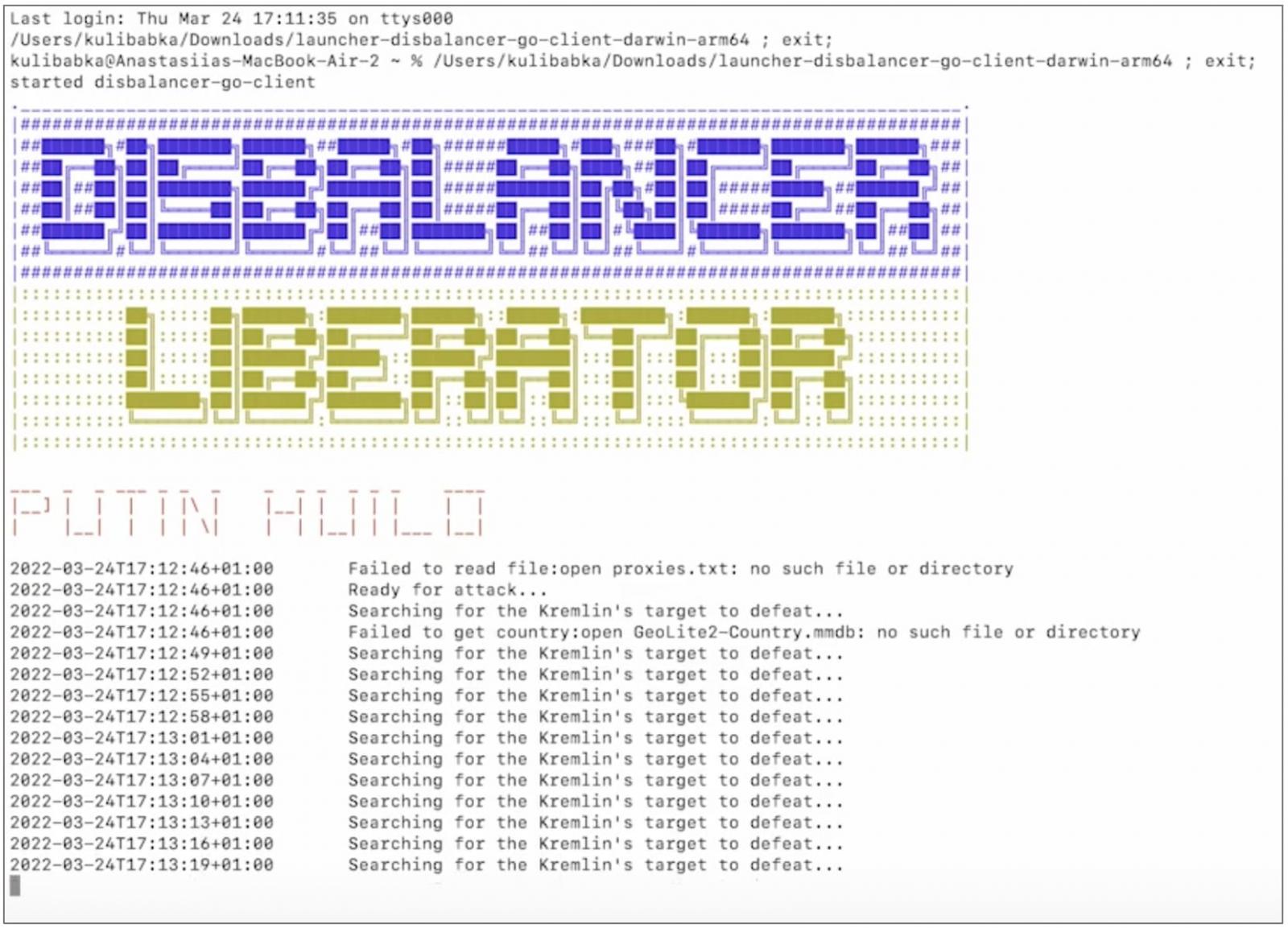
A test run of Liberator is shown below on a macOS device. As soon as the tool runs, it starts "searching for the Kremlin's target to defeat...."
The list of the websites that the tool starts to attack is curated by the disBalancer team.
Of all cyberattacks, DDoS can be fairly easy to conduct as it involves no "hacking" or breaching the target—merely flooding the servers with repeated web requests (packets) can cause them to "freeze" for some time and cease serving webpages.
This is probably why, both hacktivist groups and threat actors including ransomware and extortion gangs, have leveraged DDoS attacks against their targets at some point.
More recently, Russian hacktivist group "Killnet" has launched DDoS attacks on Romanian government sites.
YouTube's policies generally prohibit content that demonstrates how to use computers and IT equipment to conduct hacking, but the policy appears to more specifically apply to instructions on stealing credentials, compromising personal data, and causing "serious harm to others," by hacking their social media accounts.
And, that makes DDoS videos a gray area—at least on YouTube.
The legality of it all: are you at risk?
Russia's ongoing invasion of Ukraine has now lasted well over two months and the war is having devastating consequences on the Ukrainian people and their families.
A report published as recently as today shows injured civilians some with "wounds rotting with gangrene." These civilians have sought refuge in the Azovstal steel plant located in the Ukranian city of Mariupol.
While 25 of these civilians have been evacuated, unfortunately, up to 1,000 are purported to still be living underneath the plant.
The very sight of such distressing facts and footages may genuinely prompt netizens, even those based outside the Russo-Ukrainian region, to take action.
However, when conducting cyber warfare, how much are you legally in the clear, and could it backfire?
The YouTuber behind the video says he's spoken to one of disBalancer's advisors, Dyma Budorin, and explains:
"This is nothing related to anything malicious that's being done on the app but rather because of the actions of what the bot is gonna do it will start attacking Russian websites so yeah it gets flagged," Boxmining articulates his understanding of Liberator, but we are not quite sure of this claim.
Conducting DDoS attacks is a criminal offense in most jurisdictions.
Under the U.S. Computer Fraud and Abuse Act (CFAA), those found guilty of engaging in DDoS can face up to 10 years in prison. UK's Computer Misuse Act of 1990 outlaws DDoS attacks as well. And, Dutch law includes similar legislation.
Even the use of "booter services and stressers" violates these acts.
These words are not taken lightly, as the US Department of Justice has sentenced numerous people for conducting DDoS attacks in the past, including attacks against gamers, using IoT devices to conduct attacks, and for running DDoS services.
No encryption: your identity may be at risk
While the video has been praised by many, who appreciated the effort, some have raised concerns that this could be a "dangerous use" of the YouTuber's audience reach and put viewers in jeopardy.
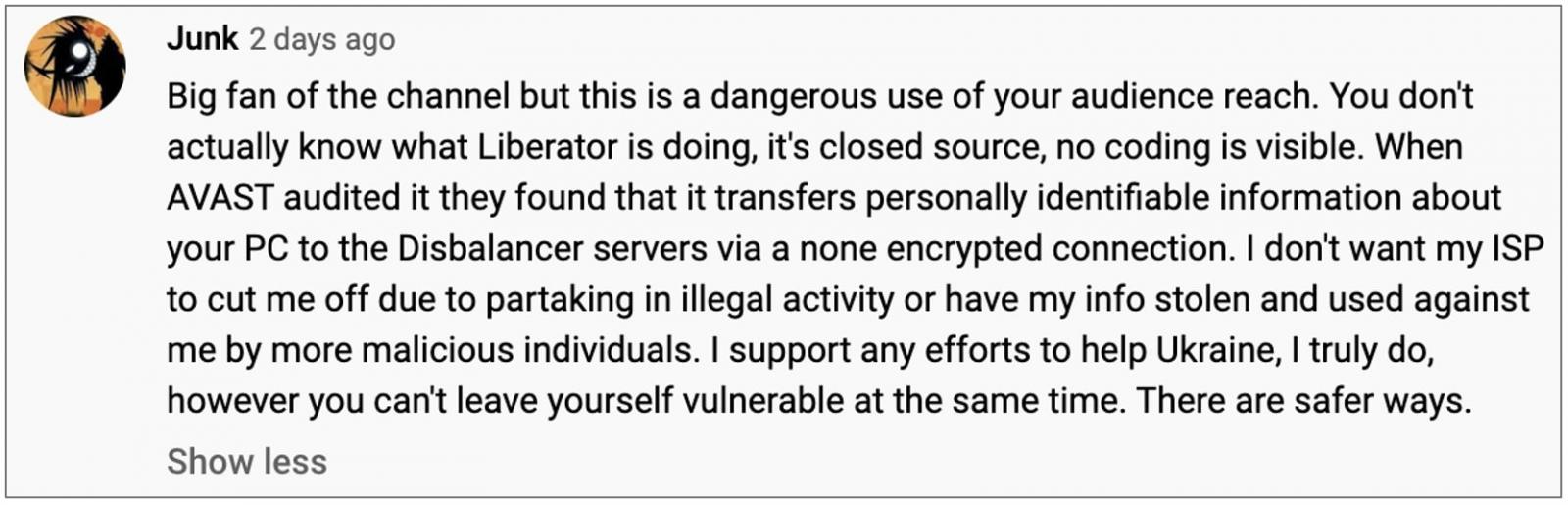
And it seems, the YouTube user Junk, may actually be right.
Last month, cyber security researchers at Avast Threat Labs warned against joining DDoS attacks against Russia as compelling as the cause may seem, and specifically looked at disBalancer's app:
"The first thing this program does is register the user, including personal information like location (derived from the IP address) and username. When the user starts the attack, this registration runs in the background without their knowledge," explains Michal Salát, Avast's threat intel director and malware analyst.
"This information runs over the unencrypted HTTP protocol to the C&C server, which means it can be easily intercepted. Additionally, there's no way to know what site you're attacking, so you have to trust the author about the sites they claim to target."
A worst-case scenario surmised by Avast Threat Labs is, should the C&C server be compromised, everyone taking part in the DDoS attack could be identified by their username and location.
"That not only would put them in danger, but they could also be tricked into attacking a different target," further explain Avast's researchers.
Radware's director of threat intelligence, Pascal Geenens also weighed in on the matter.
"Hacktivists have been anonymously promoting and educating members on how to use DDoS attack tools in the darker corners of YouTube, but an influencer with over 250k subscribers posting a professionally edited video is bringing hacktivism into a new era," Geenens told BleepingComputer in an email.
"People around the globe are volunteering their systems to be turned it into a mass DDoS weapon of destruction leveraged in a cyber conflict between nations."
"I'm sympathizing with the people who oppose war propaganda, but I'm concerned how this will evolve beyond the current conflict."
"Rules are being rewritten. Is DDoS a crime? A word of caution. Depending on the perspective, DDoS will be considered and prosecuted as a crime."
Therefore, prior to engaging in risky activities online, including hacktivism, users are advised to conduct their own research to ensure they are not violating any laws and not exposing themselves to other risks.


Comments
Shplad - 1 year ago
A very timely article for today's times. Well done. Thanks for this.
backfolder - 1 year ago
Great article, thank you Ax.
rlpaddock - 1 year ago
Revlon Cosmetics vs Logisticon, already set a precedent that sabotaged/booby trapped code is illegal, and has been for about the last 30+ years; see the Risk Digest archives. More info: "Self-Help Remedies for Software Vendors" by Henry Gitter in the January 1993 issue of The Santa Clara High Technology Law Journal.Vol 9, Issue #2. https://digitalcommons.law.scu.edu/chtlj/vol9/iss2/2/
TairikuOkami - 1 year ago
So he is promoting criminal acts against people he does not like or lesser humans so to say. Where have I seen this, oh in 1939. I do not even wanna know, what he will suggest next.
somegirlonline - 1 year ago
Never be surprised at one's lack of ability for self-preservation. I doubt that person consulted a lawyer/laws/their allies/friends except their echo chamber. When things blow up in their face(eg jail time, sued, worse etc)/some soft-brain zealot gets hyped to act, they will pull the "free speech" excuse/give a faux tearful YT apology/slink back to RL for a few months or so then come back as if nothing happened.
herbman - 1 year ago
NEWSFLASH: Mass propaganda isn't coming from Russia. The goal is to make people think it is however and it's working.
55304 - 1 year ago
Engaging in cyber warfare and not using proper protection is like having random encounters with strangers who also might be needle addicts: Not safe.
That being said, Disbalancer has put out a statement on Liberator https://blog.disbalancer.com/answer-to-bleepingcomputer-on-liberator/ TL;DR: Avast almost got it right.
That also being said, there are several tools to engage against the Russian invaders. I present to you:
"Death by a 1000 needles", which is a beautiful load balancing tool and very open source, if that is your concern:
https://github.com/Arriven/db1000n
"UA Cyber Shield" is gamifying the load balancing operation and you can work your way up the ranks from "PTN" to "Zelenskyy", if that's your thing. Comes with a nice dashboard and all.
https://github.com/opengs/uashield
Both services have built-in proxies, in case you've never heard of VPN.
And last but not least, shout-out to @ TairikuOkami and @herbman for being russian tools. Good job, guys!
See you on the battlefield.
mnf - 1 year ago
“hacktivist group, 'disBalancer,' “ as you can see in the link, they are actually a security team with specialisation in DDoS stress testing.
“works by several machines (bots)”- the software is started intentionally by the users, not automatically, so bot is not a proper term. (https://www.cloudflare.com/en-au/learning/bots/what-is-a-bot/)
Mention of Mariupol as only place of Russian aggression is a severe underestimate of the damage that was caused to Ukrainian people. It is well explained in https://blog.disbalancer.com/answer-to-bleepingcomputer-on-liberator/.(IMHO the answer sounds more professional that this article)
There are much more tools that can be used to fight against Russian government and propaganda sites.
https://github.com/danieldanielecki/IT-ARMY-of-Ukraine-Resources-in-English#distributed-denial-of-service-attack-ddos-attack-instruction
mnf - 1 year ago
It will be interesting to hear an opinion of professional lawyers, how likely someone will be charged for participating in IT army of Ukraine activities against Russian aggressors targets.