
New activity has been observed from Bitter, an APT group focused on cyberespionage, targeting the government of Bangladesh with new malware with remote file execution capabilities.
The campaign has been underway since at least August 2021 and constitutes a typical example of the targeting scope of Bitter, which remains unchanged since 2013.
The discovery and details of this campaign come from threat analysts at Cisco Talos, who shared their report with BleepingComputer.
Cisco Talos researchers attribute this campaign to Bitter based on C2 IP address overlaps with past campaigns, string encryption commonalities, and the module naming scheme.
Infection chain
During this campaign, which targets various organizations within the Bangladeshi government, Cisco has observed two infection chains, both starting with a spear-phishing email.
These messages are sent via spoofed email addresses to make them appear as if they come from Pakistani government organizations.
This was likely possible by exploiting a flaw in the Zimbra mail server that allowed attackers to send messages from a non existent email account/domain.
The difference between the two infection chains consists in the type of file attached to the malicious email: one has an .RTF and the other an .XLSX document.
The topics used in these emails relate to call records and number verification related to actual government operations.
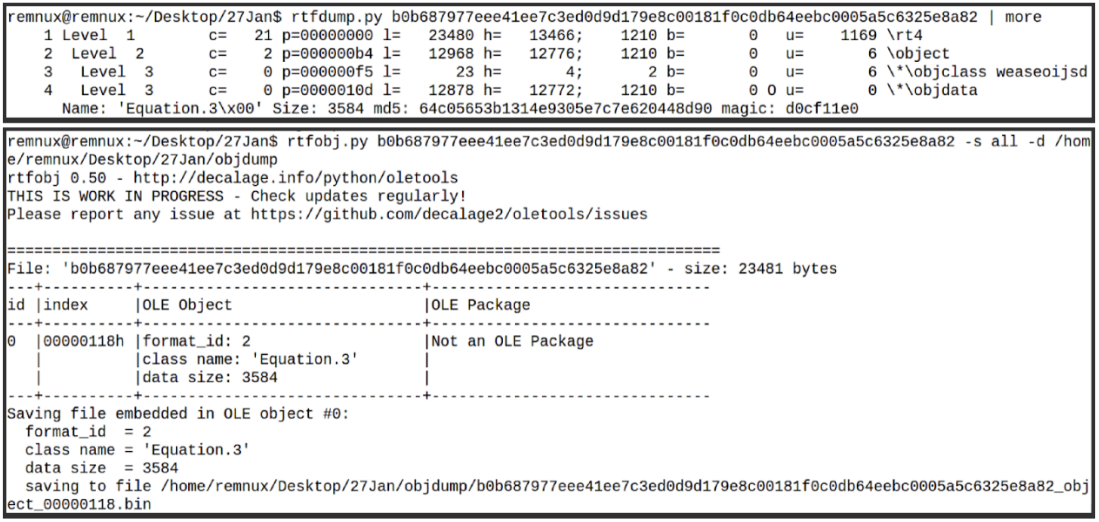
The RTF documents are weaponized to exploit CVE-2017-11882 and trigger remote code execution on machines running vulnerable Microsoft Office versions.
"When the victim opens the RTF file with Microsoft Word, it invokes the Equation Editor application and executes the equation formula containing the Return-Oriented Programming (ROP) gadgets," - Cisco Talos
"The ROP loads and executes the shellcode located at the end of the maldocs in an encrypted format that connects to the malicious host olmajhnservice[.]com and downloads the payload," the researchers explain.
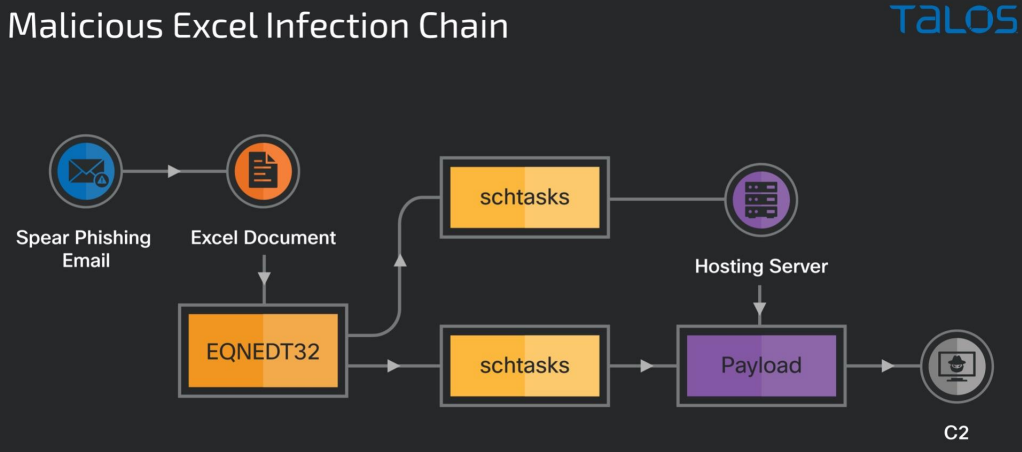
In the case of the Excel spreadsheet, opening that file triggers an exploit for CVE-2018-0798 and CVE-2018-0802, which leads to remote code execution on outdated versions of the Microsoft Office.
In this case, fetching the payload is undertaken by two scheduled tasks created by the exploit that run every five minutes after the initial infection to connect to the hosting server and download the trojan.
The ZxxZ trojan
Cisco Talos named the trojan ZxxZ. It is a 32-bit Windows executable that downloads and executes modules with generic filenames such as "Update.exe", "ntfsc.exe", or "nx.exe".
These files "are either downloaded or dropped into the victim's local application data folder and run as a Windows Security update with medium integrity to elevate the privileges of a standard user," details the report.
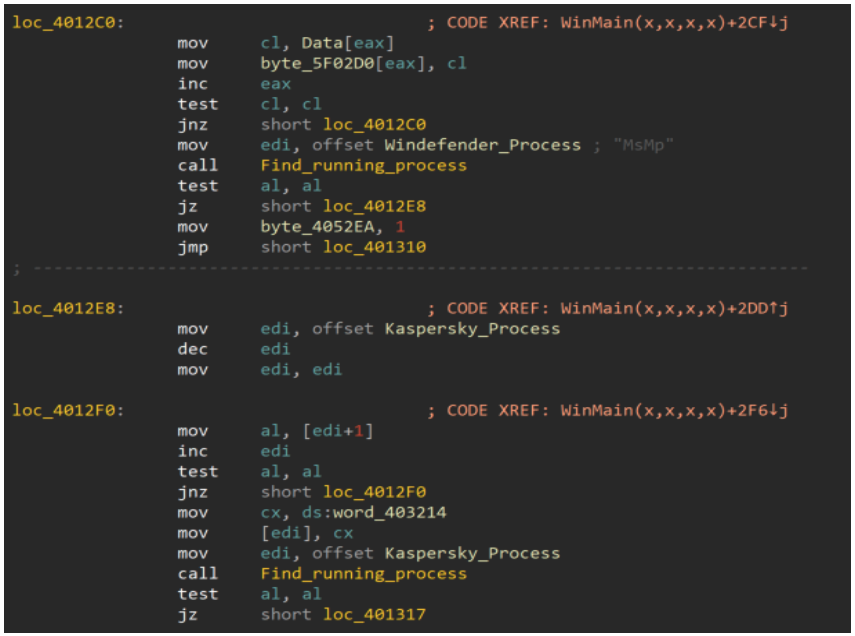
The malware features anti-detection features such as obfuscated strings, while it also searches for the existence of Windows Defender and Kaspersky antivirus processes to kill them.
After that, an info-stealing function is activated, dumping victim profiling data into a memory buffer and sending it to the command and control server (C2). The C2 then answers with a portable executable stored in "%LOCALAPPDATA%\Debug\".
In the case of a failure to fetch that executable, the ZxxZ trojan retries 225 more times before it gives up and exits.
Bitter is still out there, refreshing their arsenal with new tools and putting more effort into evading detection.
Defenders in the South and Southeast Asia are advised to use the indicators of compromise from Cisco Talos to spot and stop Bitter APT threats.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now